We got our hands on a confidential case file from some self-declared “black hat hackers”… it looks like they have a secret invite code.
Exciting introduction. Continuing on my recent binge of blue-team focused rooms, I’ll be doing the Confidential room today. From the looks of it this seems to be a very easy room. No need to get root access or run any nmap scans. In fact we don’t need to use any security-specific tools at all!
The task (The easy way)
We got our hands on a confidential case file from some self-declared “black hat hackers”… it looks like they have a secret invite code available within a QR code, but it’s covered by some image in this PDF! If we want to thwart whatever it is they are planning, we need your help to uncover what that QR code says!
Alrighty. Once we load up the machine we can access the folder containing the ‘confidential’ pdf file at /home/ubuntu/confidential .
If we open it with a normal PDF viewer you can see that the QR code is obscured with a big red exclamation mark. That’s not useful. Instead of looking for a tool to extract images I just opened the PDF in LibreOffice Draw. This is a PDF editor that comes pre-installed on the AttackBox.
After opening the PDF we can just click and drag the obstructing image out of the way, or delete it.
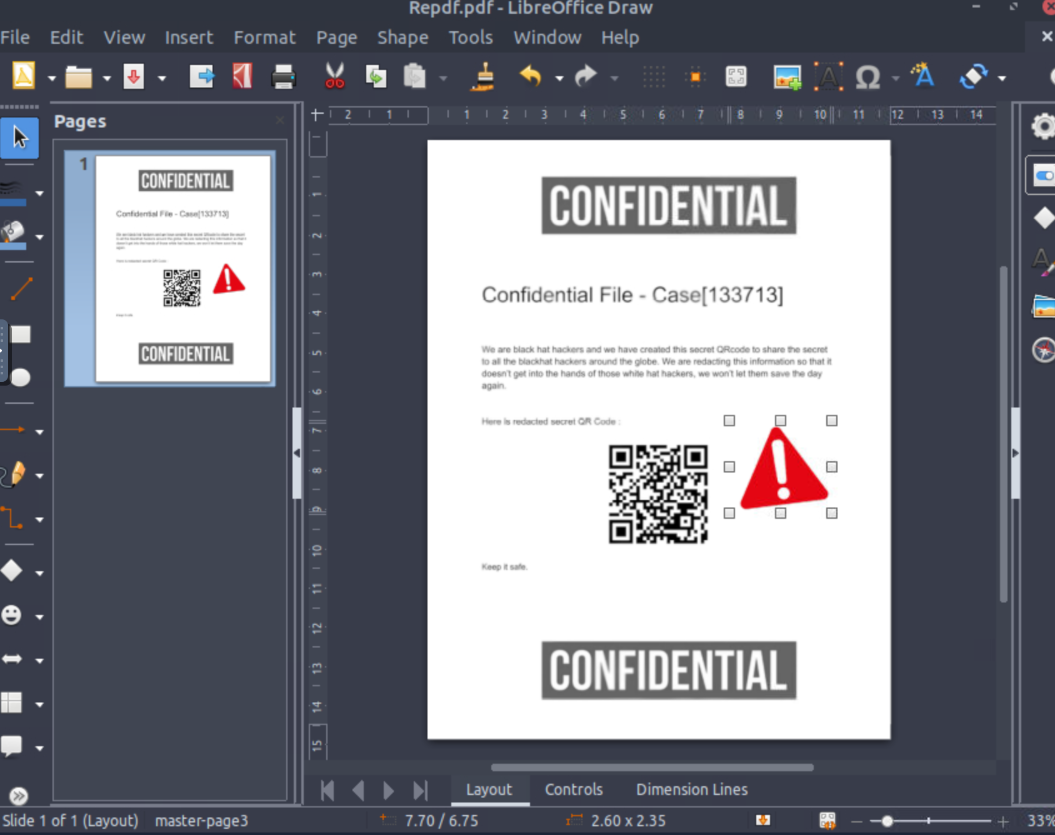
From here we can scan the PDF, and there’s the flag!
The task (The cool CLI way)
Alternatively we can do this with some forensics tools too!
pdfimages is a tool that we can use to pull out images from a PDF file. It’s simple to use with: pdfimages -j {targetpdf}
Once we’ve done this we can see all the files that have been extracted from the PDF. The one we really care about is images-000.ppm. This is the PDF without the annoying exclaimation mark covering up the QR code.
Like in the last route, we can just open up a QR Code reader and get the code by scanning the PDF. Easy!
Conclusion
There’s not really much to say here. We can get even more fancy with this and use Python to read the QR code (If we don’t have a phone handy), but…
