The corridor room on TryHackMe is an easy-level room. As the name suggests, we’ll need to look for IDORs. This should be pretty fun!
I’ve mentioned previously that I’m not the best at red-team based CTFs. I prefer the SOC analyst side of things in general, but I’m getting a lot more comfortable with these challenges.
You have found yourself in a strange corridor. Can you find your way back to where you came? In this challenge, you will explore potential IDOR vulnerabilities. Examine the URL endpoints you access as you navigate the website and note the hexadecimal values you find (they look an awful lot like a hash, don’t they?). This could help you uncover website locations you were not expected to access.
There’s a pretty helpful hint in the above text. Let’s launch the machine and run a quick nmap:
root@ip-10-201-96-172:~# nmap 10.201.24.175
Starting Nmap 7.80 ( https://nmap.org ) at 2025-08-08 10:38 BST
Nmap scan report for ip-10-201-24-175.ec2.internal (10.201.24.175)
Host is up (0.00019s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
80/tcp open http
MAC Address: 16:FF:D4:2B:D5:C1 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 0.46 seconds
Just a basic nmap scan. Nothing crazy for now. I’m not expecting there to be any other services running for an IDOR based challenge, so this should do fine.
We can go to the webpage and we’re greeted with a picture of a corridor. Fitting, I suppose.
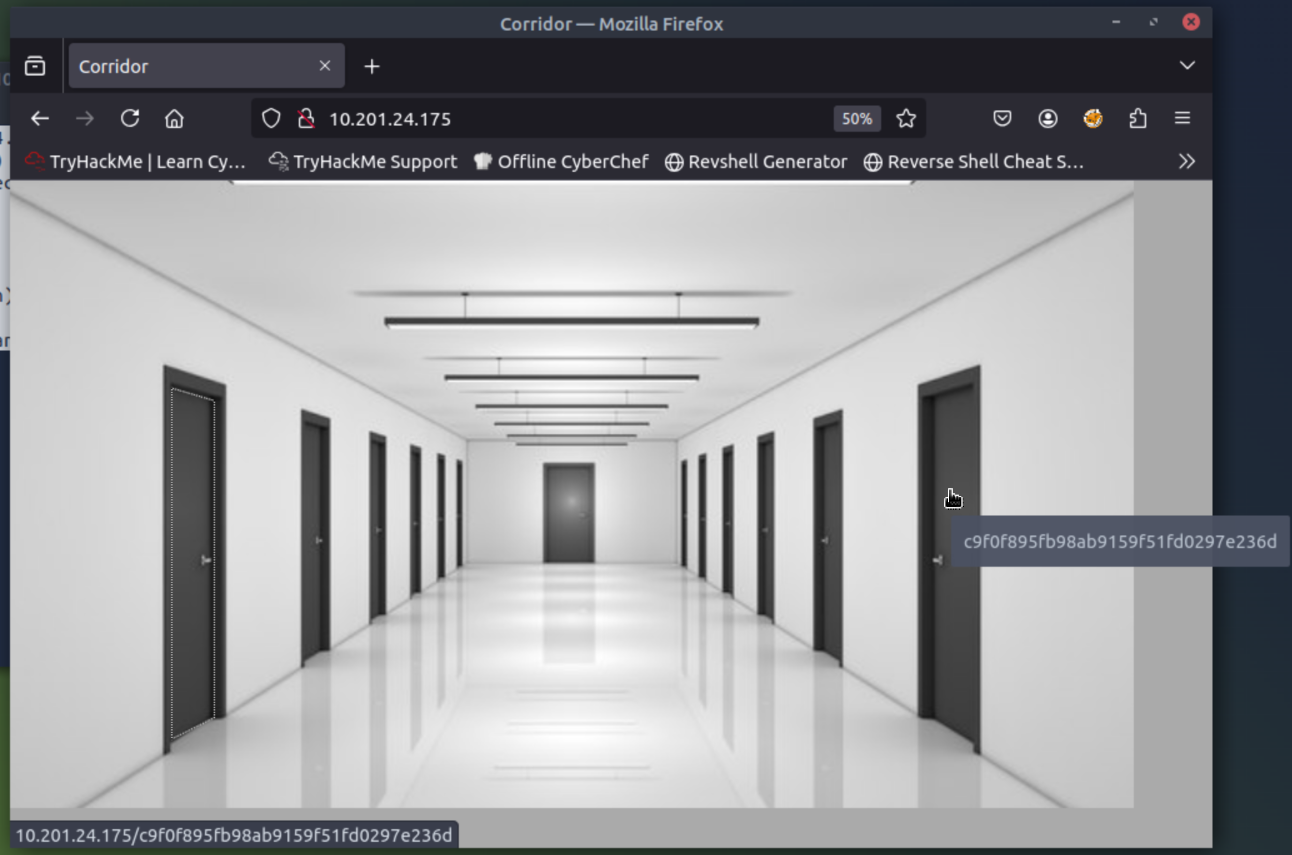 As you can see in the photo, each door has a link that looks like a hash. If we go through one of the doors (by clicking on the link) then we’re greeted with an empty room image:
As you can see in the photo, each door has a link that looks like a hash. If we go through one of the doors (by clicking on the link) then we’re greeted with an empty room image:

If we look at that room link the URL is ‘c4ca4238a0b923820dcc509a6f75849b’. Looks like a MD5 hash to me!
I put the hash through crackstation, and what do you know it’s an MD5 Hash!
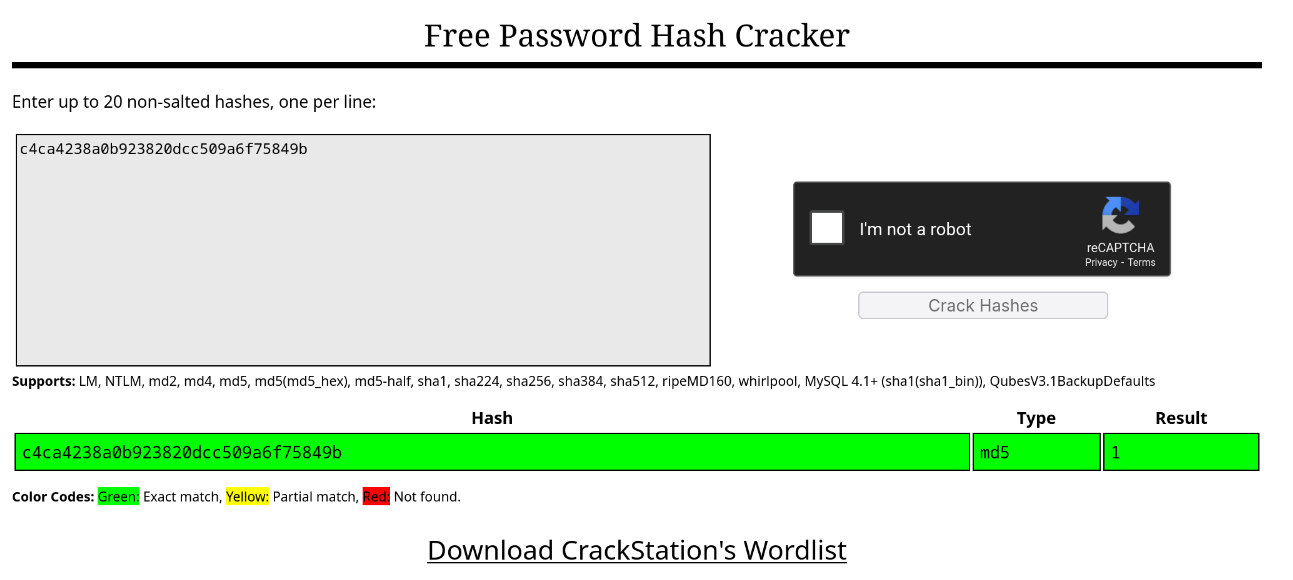
The hash is just for the number ‘1’. I decided to test this a little by running echo '1' | md5sum. Oddly I got a completely different output:
root@ip-10-201-96-172:~# echo '1' | md5sum
b026324c6904b2a9cb4b88d6d61c81d1 -
Odd.
I opened CyberChef up and tried an MD5 of ‘1’, and got the same hash that we recieved from the room link. Seems that my md5sum command is wrong. Ah well.
The text at the beginning of the room suggests where we need to navigate to get to the flag:
Can you find your way back to where you came?
Using CyberChef we can get the MD5 hash for the number ‘0’, then go to room ‘0’.

And there’s the flag!
That was easy. This was a challenge under the ‘5 minute hacks’ category, and it really does match that description.
I knew what IDOR’s were before so it was pretty simple to work this one out. I’m still a little confused why my md5sum command gave me a different output, but CyberChef came in clutch.