Introduction
If you’ve read my last post you’ll know I found a free, self-paced training resource that let you get some experience without needing to leave the house. It turns out that MasterCard has a similar virtual experience available!. These virtual experiences are all run through a platform called theforage.com which seems to offer quite a few of these.
Task one: Design a phishing email simulation
Here’s the task overview of this task:
What you’ll learn:
- What threat phishing presents to an organization
- What different types of phishing emails look like
- How Mastercard prevents and mitigates phishing threats
What you’ll do:
- Examine an obvious fake email and make it more believable
Compared to the Deloitte experience, this seems a lot more red-team-y. I’ve actually done something similar in my work - Managing and setting up internal phishing simulation emails for clients. This task gives you the opportunity to do something similar. They give a brief overview of what phishing is and how important it is to keep users aware of common phishing tricks, and how ‘An effective way to build awareness is through phishing simulation campaigns’.
The first quiz of this experience gives us a phishing email and asks what jumps out as being suspicious. Here’s the image:
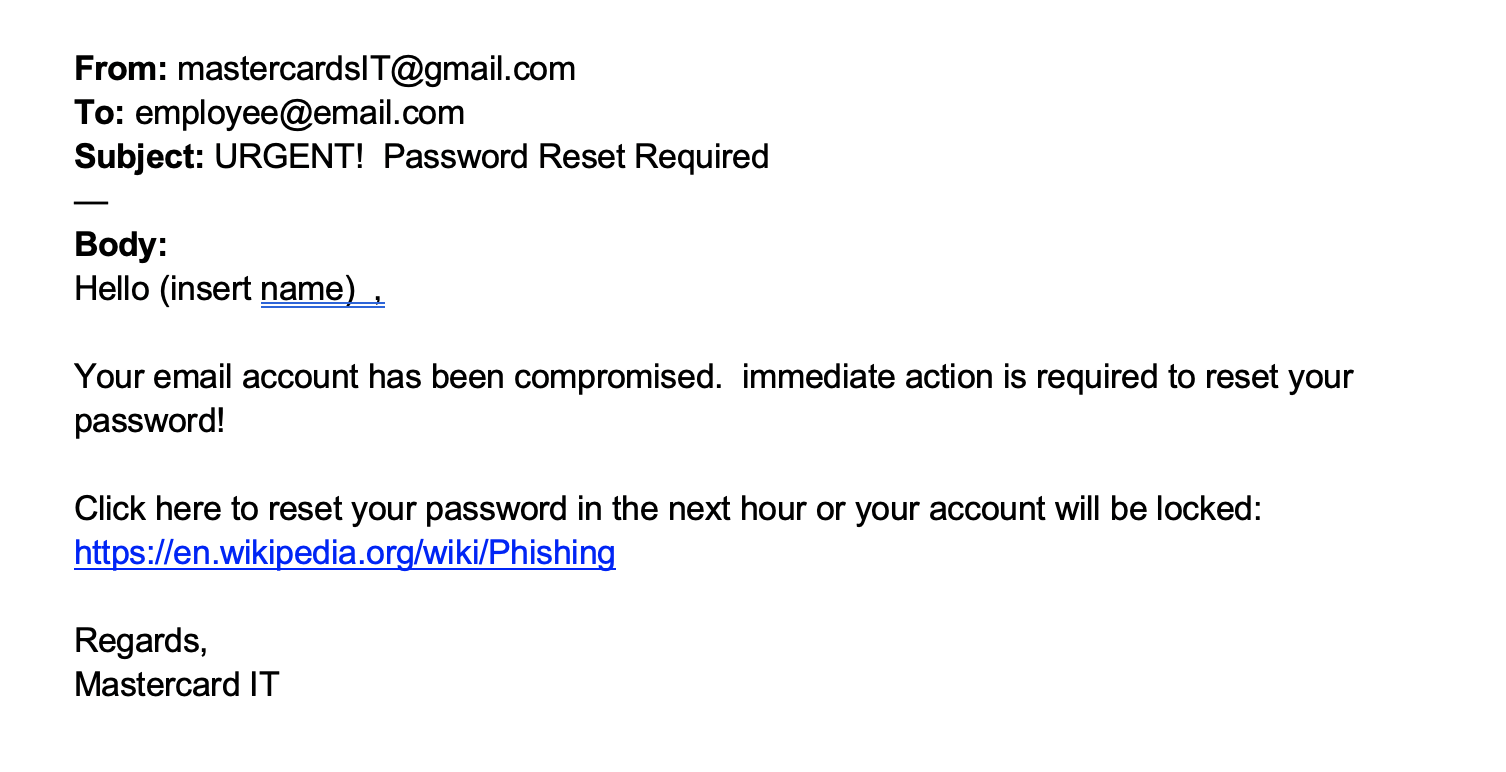 The question given is;
The question given is;
“What is the first issue you spot in this phishing email?”.
We get given a few options here and I chose the option associated with the sender email coming from a gmail account.
The second question was quite surprising:
How could you improve the body of the phishing email to make it more believable?
There are quite a few things that could be done to make the email more believable. Depending on the platform being used we could; Spoof the sender to come from someone within the organization, spoof the URL to make it look like it goes somewhere legitimate, or add some CSS.
Phishing training and simulation is a weird one. When I ran this for work I tried my hardest to avoid creating an antagonistic relationship between the security team and the recipients of the emails. As a member of the security team you want the users to notice and report the emails. You don’t want to trick them and have a gotcha moment just to gloat and be all smug when you give them training.
Phishing emails that are vague and sent from random gmail accounts do exist and are seen everyday. Spear-phishing emails are common too, but when you’re crafting simulated phishing emails they should contain obvious mistakes and errors that staff can spot. Security awareness training should be collaborative and encourage staff to report emails, not a chance for the security team to show off.
Anyway - The answer I chose was to improve the spelling and layout.
We know what an ‘obvious fake’ phishing email now looks like (as in the above task) so the next part of this task is to craft a believable phishing email.
We’re given a text box and given free reign to create a phishing email of our own. It doesn’t actually matter what you write here, as we’ve shown a better phishing email afterwards with examples of narrowing down on personalizing the email and making it look less obvious.
Task two: Interpret phishing simulation results
The learning objectives of this task are:
- How to identify which areas of the business need more awareness about phishing
- How to design and implement the appropriate training for those teams to lower our risk of an attack
In which we will:
- Create a short presentation to help teams improve security awareness
Cool. Let’s tale a look a the results from the internal Phishing test that was done:
| Team | Email open rate | Email click-through rate | Phishing success rate |
|---|---|---|---|
| IT | 80% | 2% | 0% |
| HR | 100% | 85% | 75% |
| Card Services | 60% | 50% | 10% |
| Reception | 40% | 10% | 0% |
| Engineering | 70% | 4% | 1% |
| Marketing | 65% | 40% | 38% |
| R&D | 50% | 5% | 2% |
| Overall average | 66% | 28% | 18% |
The table above does seem pretty similar to what I’ve seen on the job. Non-technical roles tend to have a higher-click through rate. It’s not expected that an HR manager would be up to date on the latest phishing techniques, but it’s good to know that staff in those roles may need some more training.
We get one question for this task:
Which teams performed poorly in the phishing simulation?
We can look at the above table to answer this.
The next part of this task is to create a presentation to show the teams identified in the previous question. This isn’t really marked or viewed by anyone, but we get some helpful hints in the next page:
- They use contextual & visual examples of how to spot phishing emails
- The presentation is clear, concise & heavy on the visuals
- They provide clear & concise action points
And that’s it complete!
We get a nice little certificate for this, and can add this to LinkedIn (Or print it out and hang it up if you want.)
Conclusion
The Deloitte job simulation focused on network logs and events, which was nice. This simulator focuses on Phishing emails - Which I’ve had hands-on experience with before. Making Phishing simulation templates too realistic will result in friction between the Security team and the rest of the company, but making them easy to spot and a collaborative event between teams will (likely) result in a better atmosphere around phishing training.