Introduction
More blue-team challenges. Hell yeah!
Today I’ll be going through the Mr Phisher room from TryHackMe.
Uncover the flag in the email attachment!
I received a suspicious email with a very weird-looking attachment. It keeps on asking me to “enable macros”. What are those?
Interesting hook. Macros are often used in phishing documents to run unintended code. Marcos are usually disabled by default because they’ve been used maliciously so often. They are useful if you have some big crazy excel sheet that runs calculations, for example.
On the more malicious side of things; I’ve seen some documents that will just have an image showing some generic looking windows error message (Like the 365 error messages) saying something like “Error: Please allow Macros to access this document.”. Y’know, normal things like that (Which you should never do.).
With all of that out of the way, let’s look at the document.
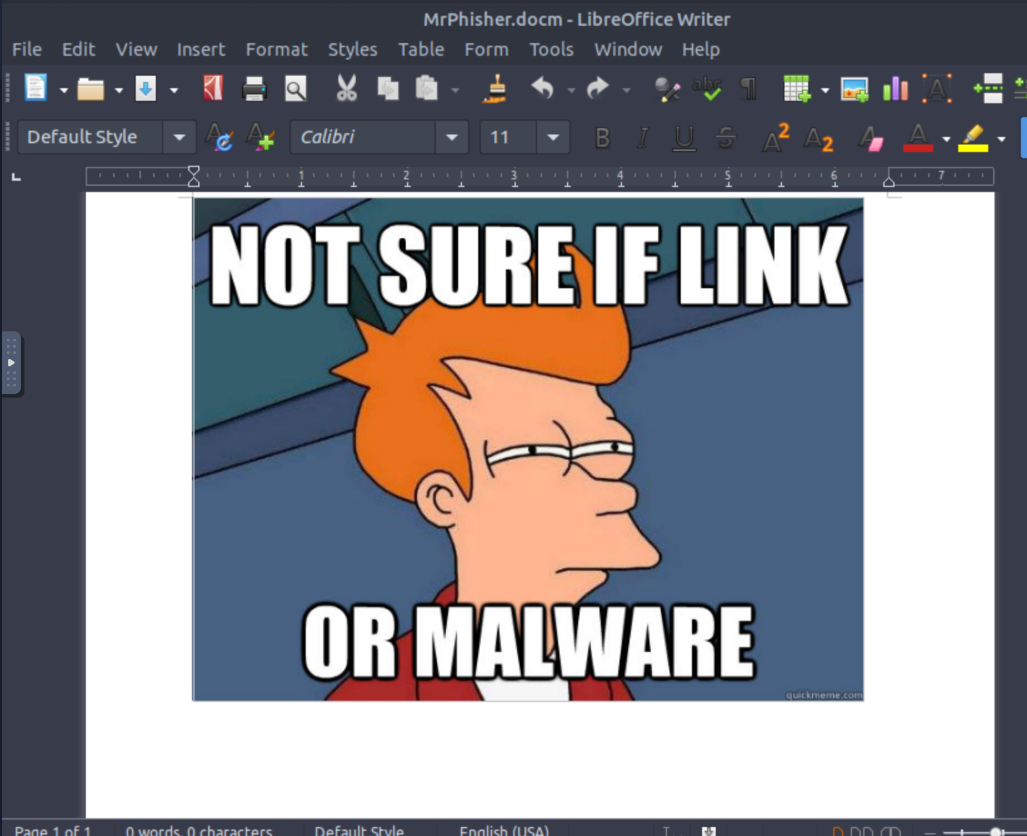 This is all that’s on the document. Just a little meme. The image gives us a little hint here, as well as the information we had above with Macros being somehow involved in this room.
This is all that’s on the document. Just a little meme. The image gives us a little hint here, as well as the information we had above with Macros being somehow involved in this room.
That’s a lie.
We actually see this when we first load the document:
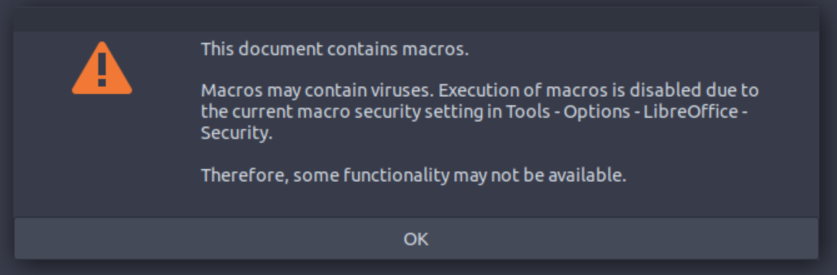 We need to enable Marcos in
We need to enable Marcos in Tools > Options > Security, adjust the ‘Macro Security’ to ‘Low’ then reload the document. Once this is done we can check the Macro that this whole room is about.
Once we’ve reloaded the document we can go to Tools > Macros > Edit Macros to view the Macro. It can be found under MrPhisher.docm > Project > Modules > NewMacros > Format. Here’s what the macro looks like:
Rem Attribute VBA_ModuleType=VBAModule
Option VBASupport 1
Sub Format()
Dim a()
Dim b As String
a = Array(102, 109, 99, 100, 127, 100, 53, 62, 105, 57, 61, 106, 62, 62, 55, 110, 113, 114, 118, 39, 36, 118, 47, 35, 32, 125, 34, 46, 46, 124, 43, 124, 25, 71, 26, 71, 21, 88)
For i = 0 To UBound(a)
b = b & Chr(a(i) Xor i)
Next
End Sub
This macro takes a list of numbers, XORs each number with its position in the list, turns the result into a character, and finally concatenates it all into our flag. The final flag string is stored in the b character.
So, how do we get the flag?
We can just run the code!
The macro itself doesn’t do anything with the b variable, so let’s add a simple print command in there.
After the loop on line 10 we can add print(b). If you want to watch it slowly appear letter-by-letter then add it on line 9.
Here’s what my final macro looked like:
Rem Attribute VBA_ModuleType=VBAModule
Option VBASupport 1
Sub Format()
Dim a()
Dim b As String
a = Array(102, 109, 99, 100, 127, 100, 53, 62, 105, 57, 61, 106, 62, 62, 55, 110, 113, 114, 118, 39, 36, 118, 47, 35, 32, 125, 34, 46, 46, 124, 43, 124, 25, 71, 26, 71, 21, 88)
For i = 0 To UBound(a)
b = b & Chr(a(i) Xor i)
Next
print(b)
End Sub
You should see the following:
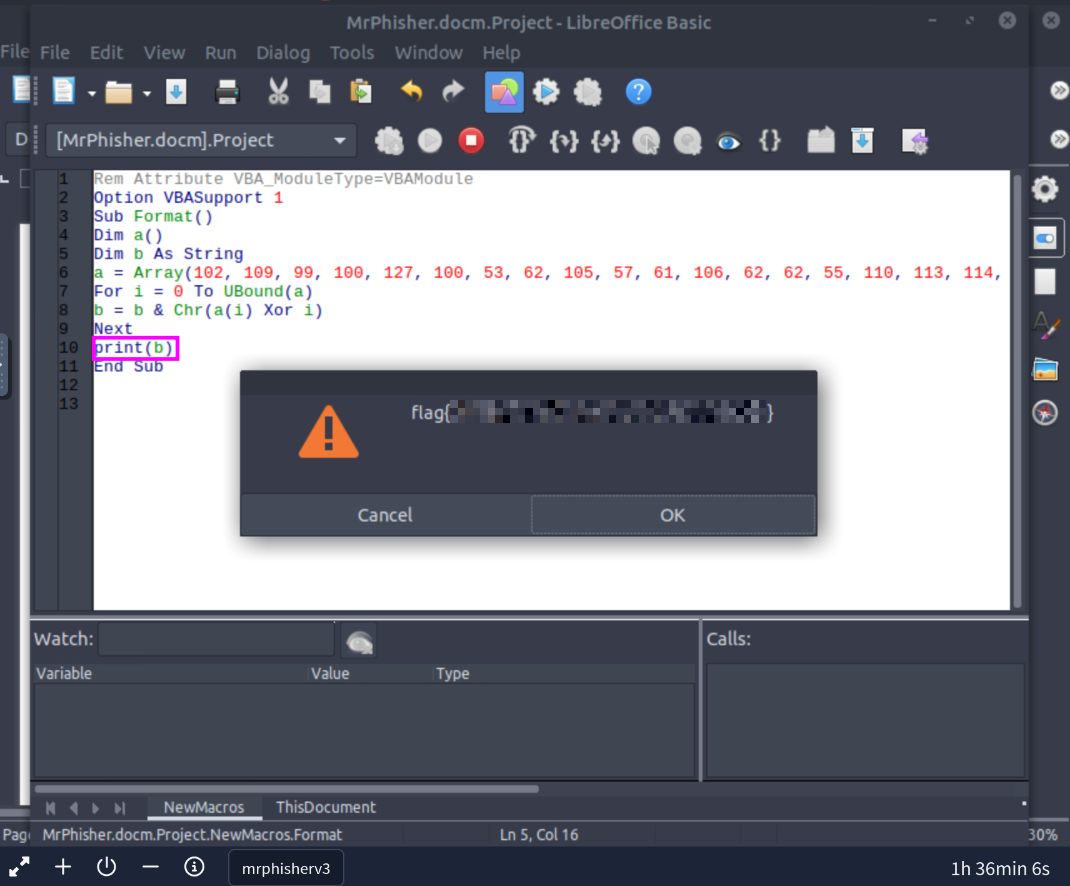 And there’s our flag!
And there’s our flag!
Conclusion
A nice simple room. The macro didn’t run a real script or have us do any further analysis of child processes. This was a nice introduction to phishing emails that are more than lures to cretential stealing websites.
I’d never suggest running a macro to check what it does. In this instance it was fine because we were in a sort of sandbox environment. Given more time I would analyze the macro line by line (where appropriate).
Anyway, another fun room! See you on the next one.