Back to CyberDefenders again today. This time doing the Oski lab.
From the looks of things this is more of a Malware analysis type lab. Here’s the description:
Analyze a sandbox report using Any.Run to identify Stealc malware behavior, extract configuration details, and map observed tactics to MITRE ATT&CK.
Let’s take a look at the scenario further!
Introduction
The accountant at the company received an email titled “Urgent New Order” from a client late in the afternoon. When he attempted to access the attached invoice, he discovered it contained false order information. Subsequently, the SIEM solution generated an alert regarding downloading a potentially malicious file. Upon initial investigation, it was found that the PPT file might be responsible for this download. Could you please conduct a detailed examination of this file?
As mentioned above, we’ll be using the any.run sandbox for this. Annoyingly though we need to create a personal account for this. If you have a business email you can sign up with that pretty easily, but if you’re like me and like to have personal accounts for things, you’ll need to flick them a message on Discord or Twitter (So much for forums).
I decided to join the Any.Run Discord and opened a ticket up to get a personal account. More on that later.
For now, let’s look at the first question:
Question one
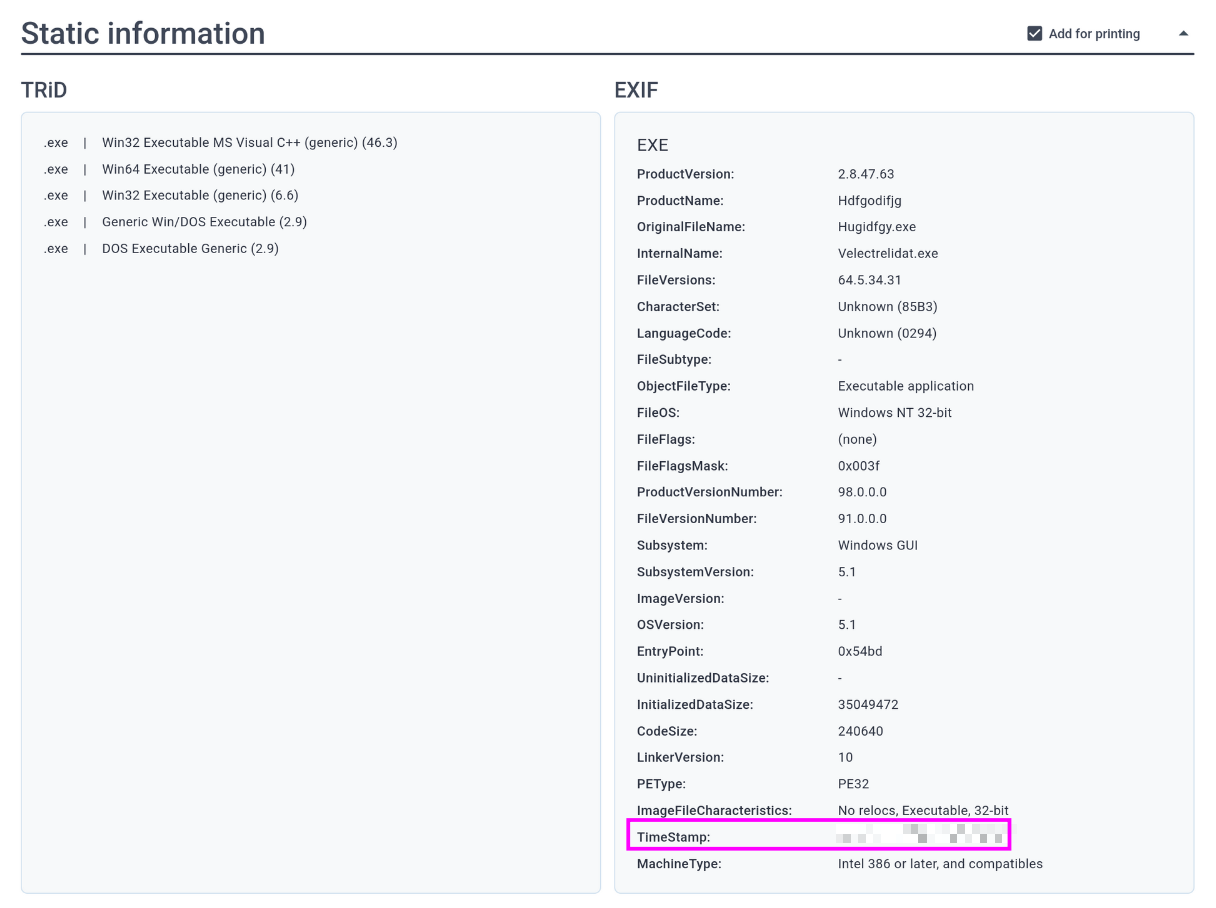
Determining the creation time of the malware can provide insights into its origin. What was the time of malware creation?
Jumping forwards a little bit, we’re actually given the report to analyze in a later question. We can open it up and take a look to get the answers for this question.
To answer the question we can check the Static Information part of the report. This part of the report shows the EXIF data for the file, which includes the TimeStamp: field:
Question two
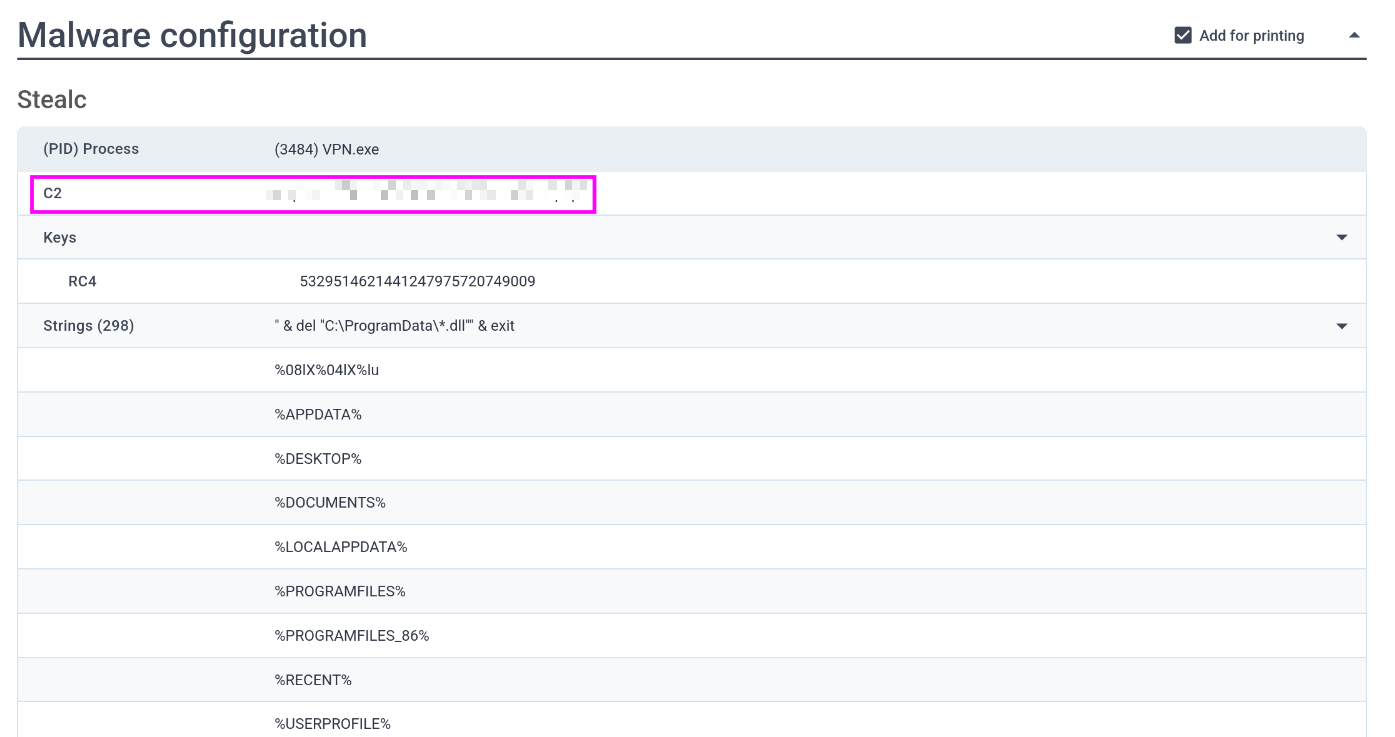
Identifying the command and control (C2) server that the malware communicates with can help trace back to the attacker. Which C2 server does the malware in the PPT file communicate with?
Still using the same report as in the above question we can check the Malware configuration section.
This gives us a lot of information to investigate and build IOCs from. Right at the very top of this section is the C2 field:
There’s the flag for this question. Here’s the next:
Quetion three
Identifying the initial actions of the malware post-infection can provide insights into its primary objectives. What is the first library that the malware requests post-infection?
There are a few different online tools that can be used for Malware Analysis. VirusTotal is probably the most well known. It’s free and anyone can sign up, weirdly it’s also recommended in this lab alongside Any.Run.
I had some trouble with this question. The question asks specifically about the library that was first requested from the malware, so we know that we’re looking for a .dll. The Behaviour activites section of the report mentions only VPN.exe under all of the categories. If we look at the strings found in the malware (Found under the Malware Configuration section) then we can actually find the answer here, just not in a linear and unambiguous way.
So let’s switch it up a little bit and head over to VirusTotal. We can search to see if anyone else has uploaded the sample using he SHA265 hash visible at the top of the report. Copy the hash (A040A0AF8697E30506218103074C7D6EA77A84BA3AC1EE5EFAE20F15530A19BB) and search for it in VirusTotal. I’ll save you some time and link the VirusTotal report here.
From here we can go to the Behavior tab and see the dropped files section. We’re able to see the .dll (and the answer) here as the first file. It’s more intuitive than Any.Run in my opinion.
There’s our answer though.
Question four
By examining the provided Any.run report, what RC4 key is used by the malware to decrypt its base64-encoded string?
A pretty simple question here. Using the Any.run report from before. We can find the RC4 key in the Malware configuration section of the report. It’s right under the C2 server we found earlier in question two.
Question five
By examining the MITRE ATT&CK techniques displayed in the Any.run sandbox report, identify the main MITRE technique (not sub-techniques) the malware uses to steal the user’s password.
MITRE techniques are useful when it comes to classifying malware, specifically in describing the Tactics, Techniques, and Procedures (TTP) observed.
We can use the Any.Run report to answer this question. In the full analysis we can check the MITRE ATT&CK details and see the following page:
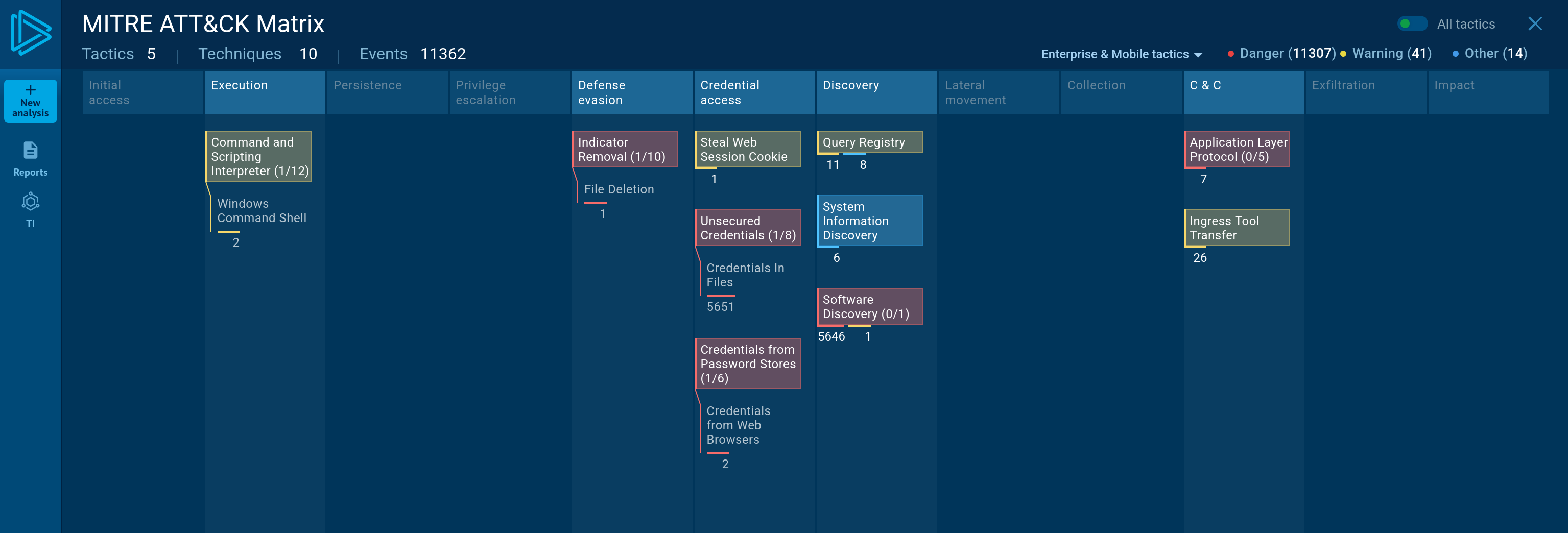
The question asks for the main technique used to steal passwords. In the above screenshot we can see that there are three techniques found under the ‘Credential access’ category. For the purpose of this question we can ignore the first two (from the top) techniques. Clicking on ‘Credentials from Password Stores’ will show us the MITRE technique number, which is the answer!
Question six
By examining the child processes displayed in the Any.run sandbox report, which directory does the malware target for the deletion of all DLL files?
We can see this answer in the ‘Strings’ under the Malware Configuration section. It’s the first string that’s shown under this section, so it’s pretty easy to spot: " & del "C:\***********\*.dll"" & exit
This command deletes every .dll file in the target directory. It’s a pretty noisy command and you could definitely build some alerts for this malware that detect every single .dll being deleted from the directory.
Bit of a tangent, but that directory was the answer.
Time to move on to the final question!
Question seven
Understanding the malware’s behavior post-data exfiltration can give insights into its evasion techniques. By analyzing the child processes, after successfully exfiltrating the user’s data, how many seconds does it take for the malware to self-delete?
The process information section of the Any.run report gives us the answer here. We can see the command that’s run:"C:\Windows\system32\cmd.exe" /c timeout /t * & del /f /q "C:\Users\admin\AppData\Local\Temp\VPN.exe" & del "C:\ProgramData\*.dll"" & exit
So what does this command do? Let’s break it down:
- Starts up CMD and waits a certain amount of time (The answer).
- Force deletes the Malware, which is located in
C:\Users\admin\AppData\Local\Temp\VPN.exe. - The final command deletes all
.dllfiles in the ProgramData directory.
The answer to this final question has been censored out, but checking the Any.run report will show you the answer. Again this is another line that you could easily write some detection rules for. Files being created and deleted from Temp directories in a short amount of time is also something suspicious that you should create alerts on.
Either way, that’s the final question answered!
Conclusion
Another easy, but pretty fun room. Any.run and VirusTotal are useful tools to know how to use. I think it’s safe to say that VirusTotal is more well known. The API is pretty easy to use and anyone can sign up for an account and start uploading samples or checking IP/File reputations.
I think that’s where I ran into some issues with this room. The room description mentions using Any.run, and the only resources that are given for the lab are the lab files.
I mentioned earlier that I submitted a ticket to Any.run (Through Discord) to get access to a personal account. Here’s the reply I got:
Hello, after reviewing your application we are unable to provide you with a free personal account as you don’t meet the criteria to receive a free personal account (Details of the criteria are not given otherwise people would say that they meet it even if they didn’t). If you want to check files for malware I recommend using services such as https://opentip.kaspersky.com/ and https://www.virustotal.com/gui/home/upload.
I find it a little annoying that we’re not given the Any.run report straight away. It’s only after scrolling down through the questions and seeing the report linked in question four that I realized we don’t actually need an account.
Still, the reply from the Any.run team was disappointing. Not mentioning the criteria because ‘people would say that they meet it even if they didn’t’ is a pretty flimsy excuse in my opinion. I’ve never seen a website gatekeep access without specifying what requirements are needed.
I’m not going to speculate on what the criteria is. I have no information to back up what the requirements are, but I did find a reddit post where someone seemingly gains access for saying that they’re a student and would like to use it. From an outside point of view it seems like getting access to a personal account is down to the discretion of whoever sees your discord ticket/reddit post.
For now I’ll stick to using VirusTotal (I mean, it’s the only thing I can use). This was a fun lab, and I’m excited to do more of them in the future.