Catch the phish before the phish catches you.
Introduction
Back to a brand new (at the time of writing) TryHackMe room. There’s been a trend of Phishing related challenges lately on this blog. Being able to recognize phishing emails, and analyze the process of what happens when a phishing link is clicked is an important tool to have as an analyst.
This challenge room is Easy. The information given is rather introductory as well, which is nice to see if you’re still starting out using THM.
As per the room, here are the basics that we need to look out for in phishing emails:
- Urgency & scare tactics: Subject lines like “Immediate action required” are designed to pressure you.
- Look-alike sender addresses: Fake domains with tiny changes (e.g., rnicrosoft.com instead of microsoft.com).
- Display name impersonation: Sender name looks familiar, but the email address doesn’t match.
- Malicious attachments: Files (DOC/XLS/ZIP) asking you to “enable macros” or containing malware.
- Compromised real accounts: Emails from hacked accounts that look legitimate but have odd requests.
- Too-good-to-be-true offers: Fake prizes, refunds, or job opportunities requiring personal details.
These are all pretty good indicators that the email we’re looking out for is malicious. This challenge room will give us a series of phishing emails for us to determine whether they’re malicious or not, before we get our flag.
Let’s start the lab up. Once it’s connected we can connect to the room at a link that looks a bit like this: https://LAB_WEB_URL.tryhackme.com/
We get given this nice website when we go to the link, basically just reiterating what we have gone over in the introduction:
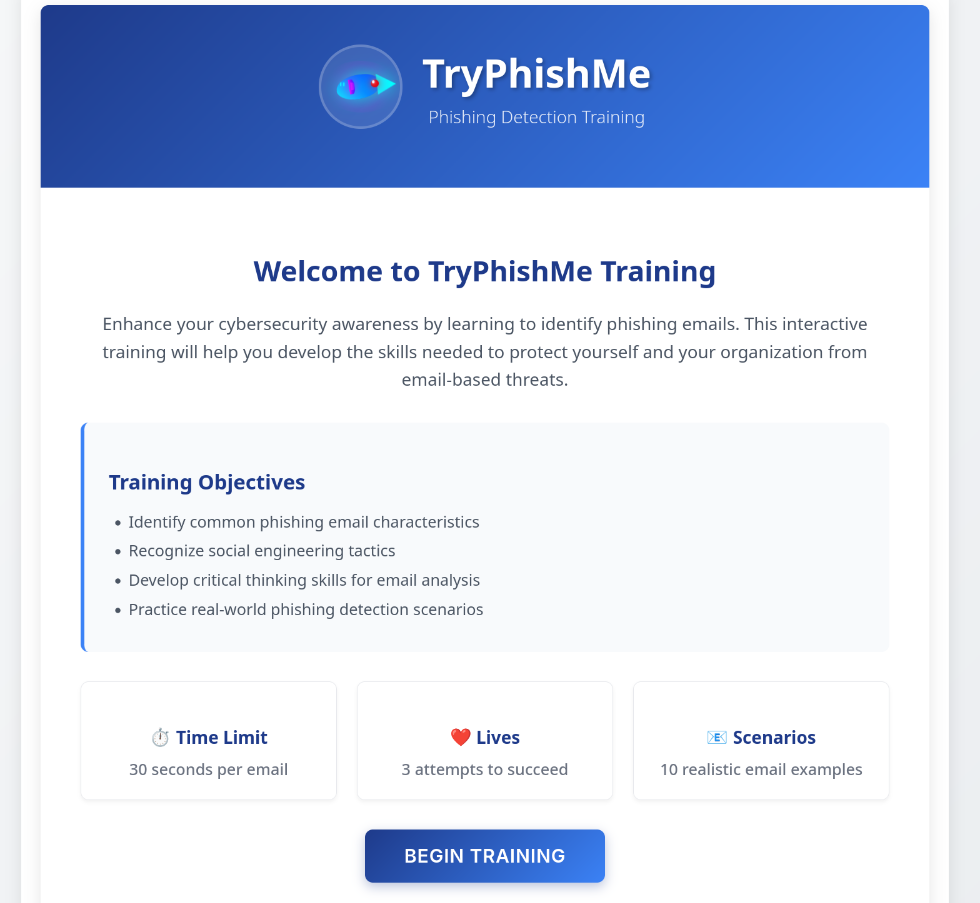
We have 30 seconds to analyze the email, 3 lives, and 10 minutes to answer all the questions.
30 seconds isn’t that much time to determine whether an email is malicious or not. Let’s see what the first one has in store for us!
Email one
From: Project Updates <updates@tryhackme.com>
To: Peter Smith <peter.smith@tryhackme.com>
Subject: Weekly team update — sprint progress
Hello Peter, here is the weekly project update. The development team completed the authentication module and began testing the reporting dashboard. No action is needed on your part; this is for your information only. Let me know if you’d like a deeper status on any task.
Unlike other rooms, in this challenge we’re taking on the role as someone who works at TryHackMe. Not a fake company like TryPhishUs or something like we’ve seen in previous challenges.
Fun.
So, let’s take a look at the From and To fields:
From: Project Updates <updates@tryhackme.com>
To: Peter Smith <peter.smith@tryhackme.com>
It will become aparent in the upcoming emails that we’re taking on the role of Peter Smith, who works at tryhackme. We can basically ignore the To field going forwards as we (Peter Smith) is always the recipient.
The next field, the From field shows us that this comes from updates@tryhackme.com. An internal sender. Business Email Compromises (BEC) is sadly pretty common, so an email coming from an internal domain doesn’t automatically mean that this is a legitimate email.
Let’s look at the body of the email to determine whether or not this is malicious or not.
There is no urgency to be seen. In fact the body of the email even says;
No action is needed on your part; this is for your information only.
We can safely mark this as a legitimate email. Onto the next!
Email two
From: HR Team <hr@external-hr-provider.com>
To: Peter Smith <peter.smith@tryhackme.com>
Subject: Updated benefits package (open to review)
Please review the attached benefits document. If it appears blank, enable macros to view the content.
The thing that jumps out immediately should be the final part of that message;
enable macros to view the content.
I have another post where we analyzed a ‘malicious’ macro to retrieve a flag.
Macros can be very useful on documents but because of how they’ve been used to run malicious scripts in the past (and how widespread this was) they are disabled by default in most environments.
It’s safer to have them disabled by default and enable on known good documents than to let random macros loose.
Anyway, we can safely say that this email is malicious.
The From field isn’t necessarily a red flag. Often the HR provider will be done through an external source if your company is small. For example if you work at a small 5-10 person company, then they likely won’t be putting the money and resources towards an HR department.
Having an external provider for HR operations can invite some risk. If the provider is breached or has their contact lists leaked then malicious actors can target those companies with an email similar to what we have above.
With all of that out of the way, we can easily answer whether this email is malicious or not.
Email three
From: Billing <billing@trustedvendor.co>
To: Peter Smith <peter.smith@tryhackme.com>
Subject: Overdue Invoice — Pay Immediately
Hello, your account shows an overdue invoice. Click https://paypel.trustedvendor-example.com/pay/12345 to make a payment.
As a reminder we only have 30 seconds to determine whether these emails are malicious or not. Usually I will write these posts as I’m doing the challenges, but more on that at the end.
The From field shows the domain of the sender: trustedvendor.co. We can assume that this is, surprise surprise, a trusted vendor.
So what does the link in the email body look like: https://paypel.trustedvendor-example.com/pay/12345.
First up, the subdomain is a misspelling/typosquat for paypal.
Next, the actual domain. We know from the From field that the expected domain from this vendor is trustedvendor.co. The domain in the email is trustedvendor-example.com.
This looks like a BEC of the trusted vendor. Shame that. I mentioned how this can happen if you outsource your HR, but of course it can also happen to vendors. You can keep your environment as secure as possible but you can’t protect everyone. Just because an account is from a known/expected source doesn’t mean it is automatically legitimate.
From that, and the scare tactic of an overdue invoice, we can safely determine the legitimacy of this email.
Onto the next one!
Email four
From: Carlos Mendes <carlos.mendes@partner.example.com>
To: Peter Smith <peter.smith@tryhackme.com>
Subject: Quick favor — can you buy gift cards?
Hey Pete, hope you’re well. I’m swamped with back-to-back calls — can you do me a quick favor? Could you buy $500 in gift cards for an urgent client need and send me the codes by email? I’ll reimburse you when I’m free.
This reads similarly to the above email. We’re not really given any information on if this is a known trusted sender with partner.example.com as the From field.
The body of the email is a dead giveaway. I’ve seen emails very similar to this pop up in real life. The request for gift cards is very odd. I’ve seen emails proporting to come from a CEO (With an email address like {company_CEO_Name@gmail.com} as the sender) with very similar wording. “I’m too busy to call but can you get me some gift cards” or something along that should raise red flags immediately.
Because we’re not given the information on whether this sender has been seen before, we can’t say for certain that this is a BEC. We can however safely note this as malicious due to the odd request.
Email five
From: Jane Doe <jane.doe@tryhackme.com>
To: Peter Smith <peter.smith@tryhackme.com>
Subject: Lunch Plans for Tomorrow
Hey Peter, do you want to grab lunch tomorrow at noon at the new Italian restaurant downtown? They have good reviews and a quieter back room for conversations. Let me know if that works for you.
Alrighty - Once again we have another internal email from someone else at tryhackme.
The body of the email doesn’t have any sense or urgency or scare tactics, that’s good! The email also references a nearby location, and is just an invite to go eat there. There’s no links or pretexting for further information. It’s pretty safe to say that this is a legitimate email.
Not much more to say here. We’re halfway through.
Email six
From: Accounts <accounts@vendor-payments.com>
To: Peter Smith <peter.smith@tryhackme.com>
Subject: Invoice INV-2025-334 (Action required)
Hi Peter, your invoice INV-2025-334 is ready. Please review and pay via https://pay.vendor-payments-secure.com/invoice/INV-2025-334.
This email reads very similar to the third email. The From field shows us that the domain is vendor-payments.com. When we look at the domain in the email body we can see that the domain there is vendor-payments-secure.com.
There is also a sense of urgency to this; An invoice is read to be paid!
We don’t know the role that Peter Smith has. Mature businesses will have a sales or supply services team that will deal with any vendor payments. It’s unlikely that a SOC analyst (For example) will personally be the one paying for vendor services.
Again we’re not given hte information to confirm whether the sender is a known contact, but based on the body of the email we are safe to mark this as malicious.
Email seven
From: Customer Support <support@survey-feedback.example>
To: Peter Smith <peter.smith@tryhackme.com>
Subject: We value your feedback — quick survey
Hi Peter, please take this short survey to help us improve: http://survey-feedback.shadylink.fake.
Let’s look at the From field again: support@survey-feedback.example.
Personally I don’t ever respond to survey links. They can be used legitimately for marketing reasons or to gauge audience reactions to a product or whatever. Like I say, I never answer these. Even if I know that the email is from a legitimate source and goes to a legitimate survey, I’ll still disregard it.
However, let’s look at the link in the body of the email: http://survey-feedback.shadylink.fake.
That’s more than enough information for us to mark this as malicious. Obviously in a real-life situation we’re not going to see shadylink.fake as a domain, but for use in this lab/challenge environment it does the job of telling us that this is a shady link.
Email eight
From: IT Notices <notices@tryhackme.com>
To: Peter Smith <peter.smith@tryhackme.com>
Subject: Planned maintenance this weekend
Hi Peter, a reminder that we will have planned infrastructure maintenance on Saturday between 01:00 and 04:00 UTC. Services may be intermittently unavailable. Please save your work and report any unexpected behaviour after the window.
Again we have another internal email. The From field is notices@tryhackme.com, which we can assume is a part of the change management at tryhackme. Usually if there are some changes being made to the environment, part of the change management process is to send out an alert to users that may be affected of any downtime.
Unrelated to this email, but still good to note, is that another part of that change management process is to have steps to revert the change. If we make a big change to our environment and then everything breaks we should have a step-by-step process for reverting the changes we made. Having these steps noted down can stop any big outages happening if somethig goes wrong.
Anywho, there’s nothing suspicious in this email. Just a notification that there will be some maintenance on infrastructure between 1am and 4am. If you’ve ever played an MMO like World Of Warcraft you’ll probably recognize messages like this.
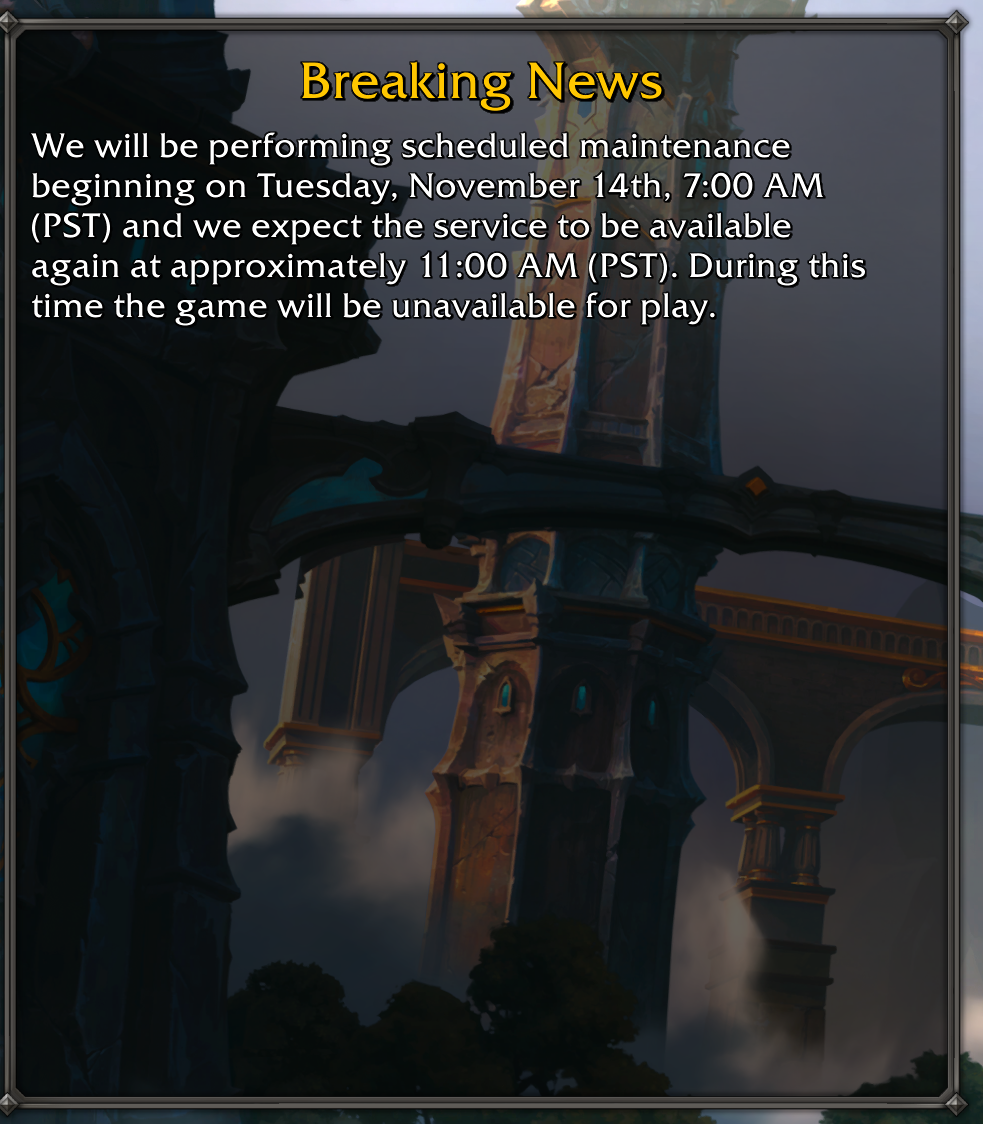
The email we’re looking at here is basically the same thing.
Email nine
From: Social Updates <no-reply@social.example.com>
To: Peter Smith <peter.smith@tryhackme.com>
Subject: Reset your password to secure your account
We detected suspicious activity. To secure your account, click https://social.example-security.com/reset and follow the steps to reset your password.
Other than tryhackme we’re not given any other business names (Except for gmail in the final email). We can’t outright say that the sender, no-reply@social.example.com is malicious. This could be from any online social service, like facebook or instagram. The From and To fields, even the Subject doesn’t give us much to go on. So let’s check the body.
The first sentence should already have alarm bells ringing. Suspicious activity on your account is a common scare tactic. A lot of people have value in their social media accounts. If those accounts are breached their reputation can be damaged, or their friends and families could fall for any messages that the attackers send.
The link included in the body diverts from the sender domain though - example-security.com is not the same domain as where the email originated from.
We have enough information here to conclude whether this is malicious or not. Let’s move on to the final email!
Email ten
From: HR - Emma Roberts <emma.roberts@gmail.com>
To: Peter Smith <peter.smith@tryhackme.com>
Subject: Please review the attached payroll correction
Hi Peter, this is Emma from HR. I’m following up about a payroll correction that requires your bank details. Please open the file attached and send your updated bank account number and sort code so I can process this change.
We know from the previous email (number two) that the HR is outsourced. The From field here shows that the sender is just using a regular old gmail account. Gmail is fine for personal use, but I’ve not ever seen a legitimate business use it. Using a business domain with gmail on the backend is common but in my experience there’s never been a legitimate business or HR enquiry done through gmail.
That’s just from the sender field, let’s look at the body of the email before we finish this.
The message states that there is an issue with payroll that needs us (Peter) to fix. There is also a file attached that we sadly don’t get access to. Thankfully we don’t need the attachment. With the sender information and the scare tactics used in the body, we can safely mark this as malicious.
Conclusion
If you’ve read some of my other posts you’ll know that I usually write these posts as I go. I’m not afraid of documenting how long I’ve gone in circles or how many rabbitholes I’ve gone down before finding the flag. Writing as I went wasn’t really feasible in this challenge. We only have 30 seconds per email to mark whether they’re malicious or not. You’d never see this in a real situation. There might be a lot of high priority incidents that come through, but pushing yourself to only take 30 seconds per incident will result in you missing some details or incorrectly marking something. The best case scenario is that you mark a legitimate email as malicious, even worse if you mark a truly malicious email as legitimate and let the end-user click on links and get their accounts compromised.
This room was fun though. There’s no hands-on tools needed, it’s purely just going off of what you’ve learned in previous rooms or just identifying emails based on experience.
I finished this challenge with 5 minutes remaining. A lot of the time was actually just me copying the emails to this post. Identifying and marking the emails only took a few seconds.
I’m always happy to see blue team focused challenges. Stay tuned for more!