Analyze malware artifacts using threat intelligence platforms like VirusTotal to identify IOCs, C2 servers, and understand adversary tactics.
Back again for another CyberDefenders lab. This time, the Yellow RAT Lab.
My previous writeup had a similar premise to this lab; Analyze a malware sample and identify the TTP, IOCs, and anything else that can potentially be used to build detection rules or map out the adversary further.
Let’s get into it!
Scenario
Here’s the introductory text we get for this lab:
During a regular IT security check at GlobalTech Industries, abnormal network traffic was detected from multiple workstations. Upon initial investigation, it was discovered that certain employees’ search queries were being redirected to unfamiliar websites. This discovery raised concerns and prompted a more thorough investigation. Your task is to investigate this incident and gather as much information as possible.
Yikes. Sounds like a pretty bad infection if this has been seen from multiple workstations. This could be evidence of a worm; a self-propagating virus that spreads from device to device doing it’s thing. It’s thing in this case appears to be a type of browser hijacker. This type of malware will redirect your search queries, usually through ad-riddled search engines, or alter search results to promote similarly malicious websites.
Over the years I’ve seen friends fall victim to malware like this, usually by ways of a browser extension that they accidentally installed. Most of the time my friends didn’t see the harm in this malware. It was seen as more of an annoyance than something they even recognized as being malware. The problem with this type of infection is that it can lead to further infections. It might just be your search queries going through some ad-filled search engine for now, but when you try to search for and download a malicious application you’ll be in deeper shit.
With all of that out of the way. Let’s take a look at the questions.
Question 0.5 - The hash
Before we answer any questions we first need to get the information on the malware sample we have. We’re not actually given a sample of the malware, but if you unzip the lab file we’re given you’ll see this:
~/Downloads> cat temp_extract_dir/hash.txt
malware hash: 30E527E45F50D2BA82865C5679A6FA998EE0A1755361AB01673950810D071C85
Use this hash on online threat intel platforms (e.g., VirusTotal, Hybrid Analysis) to complete the lab analysis.
Wonderful. So we have our filehash and a few recommendations on which threat intel tools to use for our analysis. Now we can answer some questions.
Question 1
Understanding the adversary helps defend against attacks. What is the name of the malware family that causes abnormal network traffic?
This question took me a day to find the answer. In the time it took me to find the answer for this question, I had inadvertently found the rest of the answers for this lab. That isn’t a bad thing though. A big part of Cybersecurity is spending time doing research. Blue and Red teams will all spend hours researching and going down rabbit holes throughout their careers.
Getting stuck on this question led me down plenty of rabbit holes. Some of them were useful as I’ll touch on later, while others left me wondering why I spent 10 minutes looking through someone’s VirusTotal profile.
Quick aside here to mention the hints available for this question, and my thoughts on using hints in general. I’ve seen plenty of comments and messages asking whether gettings hints is bad, or telling other people they’re ‘bad’ hackers if they need to use hints on CTFs. It’s important to remember that all the labs on these platforms are written by someone who already knows the answers. If, like in this lab, they are relying on third parties to provide you the answer (like VirusTotal or Hybrid Analysis) then those answers may be aparent when the lab is written in 2020, for example, but by 2025 the UI or even the data on the page may have changed so much that the answer isn’t aparent anymore. Using the available hints in a room doesn’t make you better or worse than someone who finds the answer straight away. We’re all learning and you won’t know everything straight away. The hints are there to help you. What I wouldn’t suggest is looking for the answers on some blog somewhere. You learn nothing by finding the answer, but you learn from using hints. So just use hints.
The three hints for this question are;
Hint 1
Start by uploading the provided hash to VirusTotal. Have you explored the different sections that are available for analysis?
Hint 2
After uploading the hash to VirusTotal, navigate to the Relations tab and explore the Graph Summary. This will help you visualize the relationships and associations of the file.
Hint 3
In VirusTotal, under the Relations tab, find the Graph Summary and select the PEDLL icon. Use the Visualization to view the Tree representation, where you will see how the malware is detected and linked to the family.
All three of these hints point us towards VirusTotal, so let’s look at the page for this hash. If we follow the hints and go to the Relations tab and then to the graph summary, then we’re not given much.
Here’s what I saw:
This and any other information on these graphs didn’t tell me anything about the malware family. On the Relations tab (And the other tabs as well) there are some malware classifications mentioned - pedll. This doesn’t match the format of the answer being ****** ******** ***.
From here I took a look through the comments availabe in the community tab. Adding comments and notes to malware samples, IPs and other malicious indicators is useful. I have a tool that lets me automate this pretty easily. You can add as much detail as you want in comments, like when you first saw this IOC, what type of industry it was seen being used against, and plenty of other useful information that would assist other threat researchers.
If you look through the comments on common malware samples you’ll see a lot of automated comments as well. I’ve started to recognize usernames from accounts that no doubt have added tools that utilize the VirusTotal API to automatically report IOCs.
I took a look through the comments before deciding to change it up a bit and use another site. In one of the comments I saw this threat.rip upload of the file. Maybe they have some more useful information?
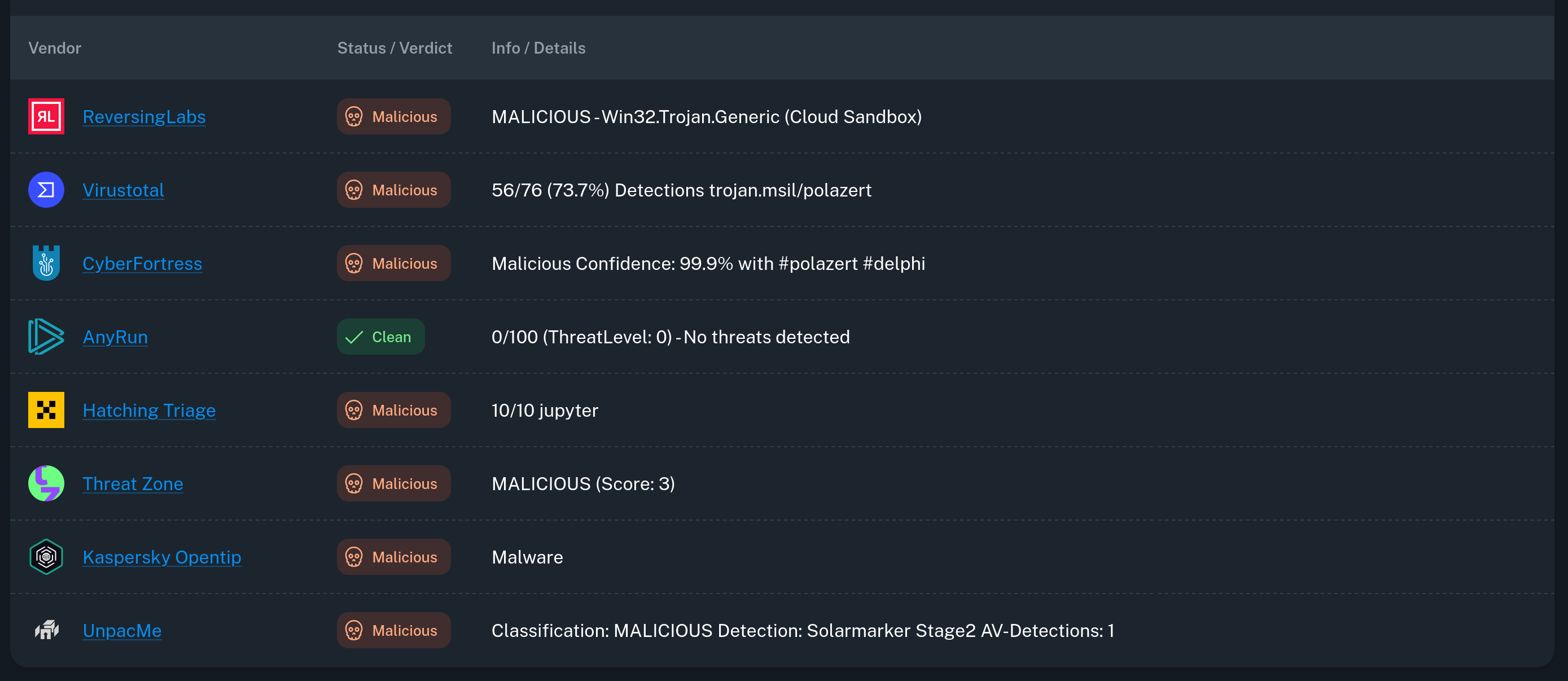
Unfortunately this report was lacking the malware family that the question is looking for. It did show that Any.Run classified this as clean, which was a bit funny given what we know about the malware.
After checking Hybrid Analysis I again came to a dead end. There weren’t any malware classifications on any of the sites that I found which matched the format of the answer. While going through the rabbit holes of various threat intel sites, I found this report by redcanary. It’s a pretty interesting read and gives us a nice rundown of what the malware does. This report is very well written and easy to digest, and most importantly it also contains almost all of the answers coming up.
But where do we find the answer? I set about scrolling through the VirusTotal comments looking for anything that might lead me on the right path. *Eventually I found a single comment that matched the format of the answer, and that was it.
If you’re reading this and you’re as stuck as I was. Look at the name of the report, then of the lab.
Question 2
As part of our incident response, knowing common filenames the malware uses can help scan other workstations for potential infection. What is the common filename associated with the malware discovered on our workstations?
Now that we’ve found that RedCanary report we can use it to help answer the questions. This answer can also be found in VirusTotal, but I found the layout of the RedCanary report to be much nicer.
We’re looking for a common filename that the malware uses. If you scroll down in the report to Deep dive on the .NET RAT we can see that a .dll file is used by the malware to action a lot of malicious activity. The name of that .dll file is our answer.
Question 3
Determining the compilation timestamp of malware can reveal insights into its development and deployment timeline. What is the compilation timestamp of the malware that infected our network?
This is another answer that we can find back on the VirusTotal page.
In the details page we can see a History subheading that lists useful information like; Creation Time, First Seen In The Wild, First Submission, Last Submission, and Last Analysis.
Compared to the first question this one was fairly easy. Onto the next!
Question 4
Understanding when the broader cybersecurity community first identified the malware could help determine how long the malware might have been in the environment before detection. When was the malware first submitted to VirusTotal?
Again, this is another very easy question to answer. We can use the details in the same History subheading from the previous question to get this answer.
Question 5
To completely eradicate the threat from Industries’ systems, we need to identify all components dropped by the malware. What is the name of the .dat file that the malware dropped in the AppData folder?
This question is where the RedCanary report really comes in handy. The VirusTotal report will show that the only dropped file is authrootstl.cab. This is not correct.
The RedCanary report goes a bit more in-depth and mentions the .dat file. You can CTRL + F for .dat to quickly find the answer, but I definitely recommend reading through the whole report. It’ll help for the next question as well as just being a well written report.
Either way, use the RedCanary report.
Question 6
It is crucial to identify the C2 servers with which the malware communicates to block its communication and prevent further data exfiltration. What is the C2 server that the malware is communicating with?
The VirusTotal report has Contacted URLs and Contacted Domains subheadings in the Relations tab. However neither of these actually mention the C2 server.
At the bottom of the RedCanary report we see that during the initial check in with the C2 server the following information is sent:
hwid: the randomly generated value stored in %USERPROFILE%\AppData\Roaming\**********.dat
pn: computer name
os: Windows OS version
x: host machine architecture (x64 or x86) based on the running process
prm: the permission level of the the running process (admin or user)
ver: malware version. Fixed string: DN-DN/FB1
wg: computer workgroup
That’s some pretty juicy information for an attacker to have. Right above this part of the report is a defanged version of the C2 server.
And that’s our final answer (The defanged version).
Conclusion
That was fun. As I mentioned, the first question took me a long time to find. Malware Families are usually listed at the top of VirusTotal reports, and throughout my searching I got pretty lucky in finding a random comment with the answer. I think the question itself could use some editing as the answer isn’t widely recognized as the actual malware family, but other than that the rest of the questions were a breeze.
Using multiple sources and researching for a while isn’t a bad thing. Threat Research takes time there aren’t any easy low-hanging fruit to find in real scenarios. Ultimately I liked this lab!